xsserve
Simplify XSS exploitation
xsserve
🚀 Usage
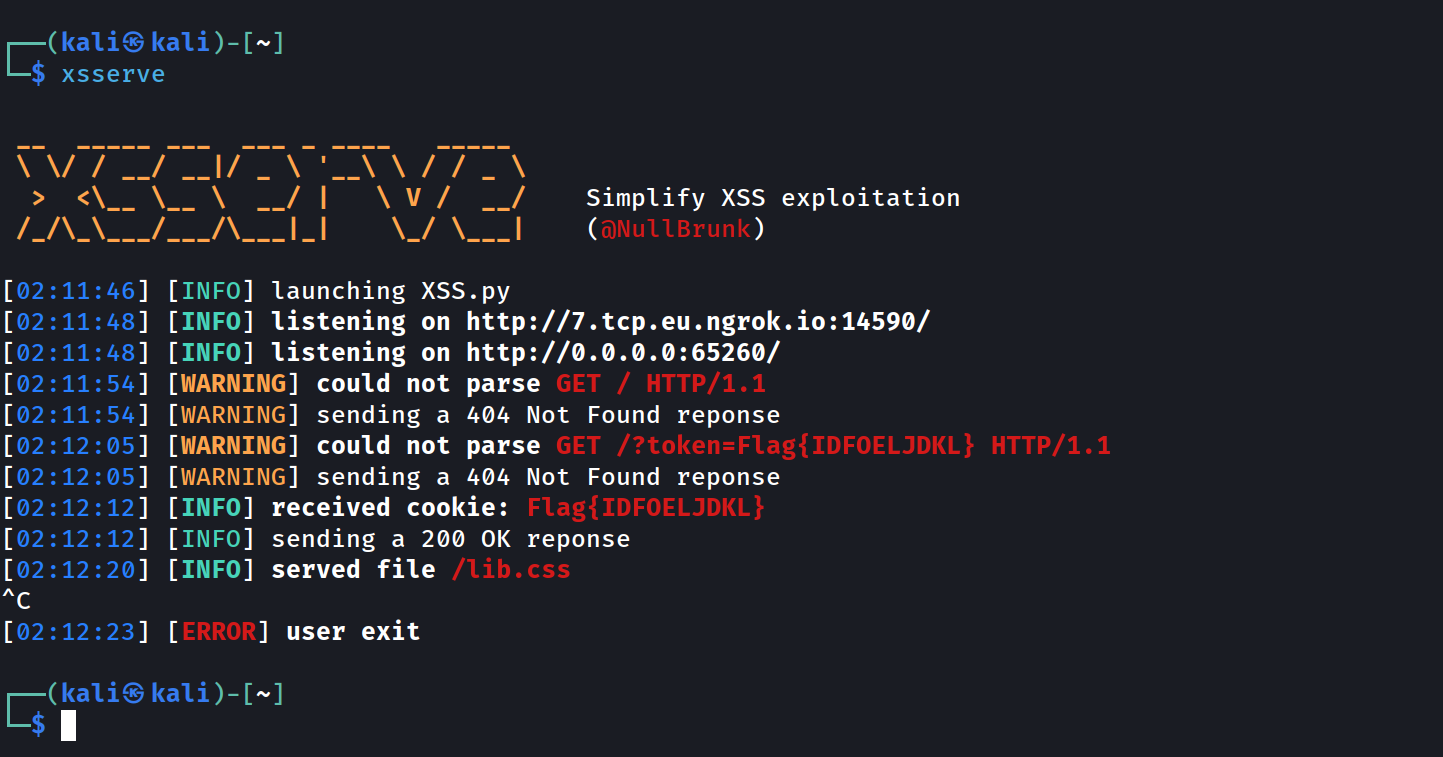
This tool simplifies XSS exploitation by combining a socket-based HTTP server with the power of ngrok.
It enables you to quickly launch a local server and make it publicly accessible, making it easier to share payloads or demonstrate XSS vulnerabilities.
There are basically three endpoints:
| Endpoint | What does it to |
|---|---|
/FILENAME |
Serves the file named FILENAME in the files/ directory, like a standard HTTP server. |
/* |
Logs any access to other endpoints directly in your console, giving you full visibility into unexpected requests. |
Ideal for pentesters, security researchers, and cybersecurity enthusiasts who need a lightweight and versatile tool for XSS testing. Some CLI argument are provided to enhance user experience:
| Argument | What does it to |
|---|---|
-v, --verbose |
By default, only the first line of every request and the body are printed. With -v, all headers sent along with the request are also printed |
-p, --port |
By default, xsserve listens on a random port between 65000 and 65100. With -p you can specify a custom port |
-n, --ngrok |
Launches an ngrok tunnel that listens on the xsserve port. Ngrok provides a public address, which is useful if you don’t have a VPS or don’t want to set up port forwarding. |
Source
The source code and installation instructions are accessible here.
This post is licensed under
CC BY 4.0
by the author.